EDIT: I solved it. See post 2 for the solution if you're in a similar boat and find this via a search engine or the forum's search facility. Feel free to PM me with any questions or reply below. 
I have just upgraded our x86 edge router to a re-purposed Dell Optiplex 7010 (4c8t Core i7 3770 @ 3.4GHz, 8GB DDR3 dual channel, 128GB SSD, Intel Pro 1000 VT quad port NIC). It's running Arch Linux with the linux-hardened kernel, using dnscrypt-proxy for DNS, dhcpd for DHCP, and Shorewall for NAT/firewall. I have the local network split so that my NAS and 4k CCTV cameras are on a separate interface and subnet (aka a 'DMZ' of sorts). The topology looks like this (except the second switch is now a Netgear ProSafe GS108):
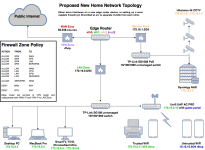
The router itself has three of its ports physically connected (WAN, LAN and DMZ) and also connects to my VPN provider over WireGuard using virtual interface 'azirevpn-uk1'. If you're unfamiliar, WireGuard is a very small, fast and secure VPN protocol and behaves exactly like any other Linux interface. Don't let it being a VPN lead you down the mental garden path if you're unfamiliar. Treat it as any other interface (i.e. you use ip add, ip route etc as normal). The router is thus connected to my VM internet as well as the VPN over WireGuard. The LAN clients can therefore connect only to WireGuard via the router, and the DMZ is open to the internet via VM.
To tunnel the LAN via the WireGuard VPN I needed to manually set the routes after bringing up the interface (else the VM WAN/ISP link would be default). I did this by adding a table as so:
Now the LAN clients all only get online via the VPN but the DMZ is free to serve over the net (so my domain still works when connecting to Plex etc). So far, so awesomesauce.
Unfortunately (for me) I have a dilemma. When the LAN is set up thus, all LAN traffic does indeed get tunneled through my VPN, but there's no route to the DMZ subnet so that LAN clients can watch Plex (for example). If I take down the WireGuard interface and delete the 'VPN table' route rules everything works again, and LAN clients can resolve and display content from the DMZ servers. This is of course because the router's default routing table allows subnets to talk to each other, but the VPN table I made doesn't - it only has one route, to the VPN tunnel.
I've learnt a LOT about networking in the last week (hence being able to build this router by hand myself and write all the conf files to get it working), but I'm still learning a lot - including routing. This is definitely a routing issue btw, as Shorewall is set up with policies to allow communication from LAN to DMZ (even though the reverse is disallowed for obvious reasons). Everything works if I remove the VPN and it's default routing entry (which again, doesn't include a rule for anything other than 'send all traffic to the VPN', so this is expected behaviour).
What's my best option here? I basically need to add a rule for LAN to say 'Yes tunnel everything, unless it's a request for 192.168.2.0/24 as that's local - ask the router at 192.168.1.1 instead'. Is it as simple as not setting the VPN table's dev azirevpn-uk1 route as default and then also adding a second route for 192.168.2.0/24 via 192.168.1.1 (the LAN's router IP)? If so which rule is default, azirevpn-uk1 or the one for 'all other traffic to the router for it to decide'? Or something else? Any help greatly appreciated. Thanks in advance!

I have just upgraded our x86 edge router to a re-purposed Dell Optiplex 7010 (4c8t Core i7 3770 @ 3.4GHz, 8GB DDR3 dual channel, 128GB SSD, Intel Pro 1000 VT quad port NIC). It's running Arch Linux with the linux-hardened kernel, using dnscrypt-proxy for DNS, dhcpd for DHCP, and Shorewall for NAT/firewall. I have the local network split so that my NAS and 4k CCTV cameras are on a separate interface and subnet (aka a 'DMZ' of sorts). The topology looks like this (except the second switch is now a Netgear ProSafe GS108):

The router itself has three of its ports physically connected (WAN, LAN and DMZ) and also connects to my VPN provider over WireGuard using virtual interface 'azirevpn-uk1'. If you're unfamiliar, WireGuard is a very small, fast and secure VPN protocol and behaves exactly like any other Linux interface. Don't let it being a VPN lead you down the mental garden path if you're unfamiliar. Treat it as any other interface (i.e. you use ip add, ip route etc as normal). The router is thus connected to my VM internet as well as the VPN over WireGuard. The LAN clients can therefore connect only to WireGuard via the router, and the DMZ is open to the internet via VM.
To tunnel the LAN via the WireGuard VPN I needed to manually set the routes after bringing up the interface (else the VM WAN/ISP link would be default). I did this by adding a table as so:
Code:
echo "10 vpn" >> /etc/iproute2/rt_tables
Code:
ip rule add unicast iif enp3s0f0 table vpn
Code:
ip route add default dev azirevpn-uk1 via 10.xx.xx.xx table vpnNow the LAN clients all only get online via the VPN but the DMZ is free to serve over the net (so my domain still works when connecting to Plex etc). So far, so awesomesauce.
Unfortunately (for me) I have a dilemma. When the LAN is set up thus, all LAN traffic does indeed get tunneled through my VPN, but there's no route to the DMZ subnet so that LAN clients can watch Plex (for example). If I take down the WireGuard interface and delete the 'VPN table' route rules everything works again, and LAN clients can resolve and display content from the DMZ servers. This is of course because the router's default routing table allows subnets to talk to each other, but the VPN table I made doesn't - it only has one route, to the VPN tunnel.
I've learnt a LOT about networking in the last week (hence being able to build this router by hand myself and write all the conf files to get it working), but I'm still learning a lot - including routing. This is definitely a routing issue btw, as Shorewall is set up with policies to allow communication from LAN to DMZ (even though the reverse is disallowed for obvious reasons). Everything works if I remove the VPN and it's default routing entry (which again, doesn't include a rule for anything other than 'send all traffic to the VPN', so this is expected behaviour).
What's my best option here? I basically need to add a rule for LAN to say 'Yes tunnel everything, unless it's a request for 192.168.2.0/24 as that's local - ask the router at 192.168.1.1 instead'. Is it as simple as not setting the VPN table's dev azirevpn-uk1 route as default and then also adding a second route for 192.168.2.0/24 via 192.168.1.1 (the LAN's router IP)? If so which rule is default, azirevpn-uk1 or the one for 'all other traffic to the router for it to decide'? Or something else? Any help greatly appreciated. Thanks in advance!
Last edited:



 But now I know, and it's great.
But now I know, and it's great. Just kidding. From what I read, 600Mbit+ is possible in synthetic testing:
Just kidding. From what I read, 600Mbit+ is possible in synthetic testing: