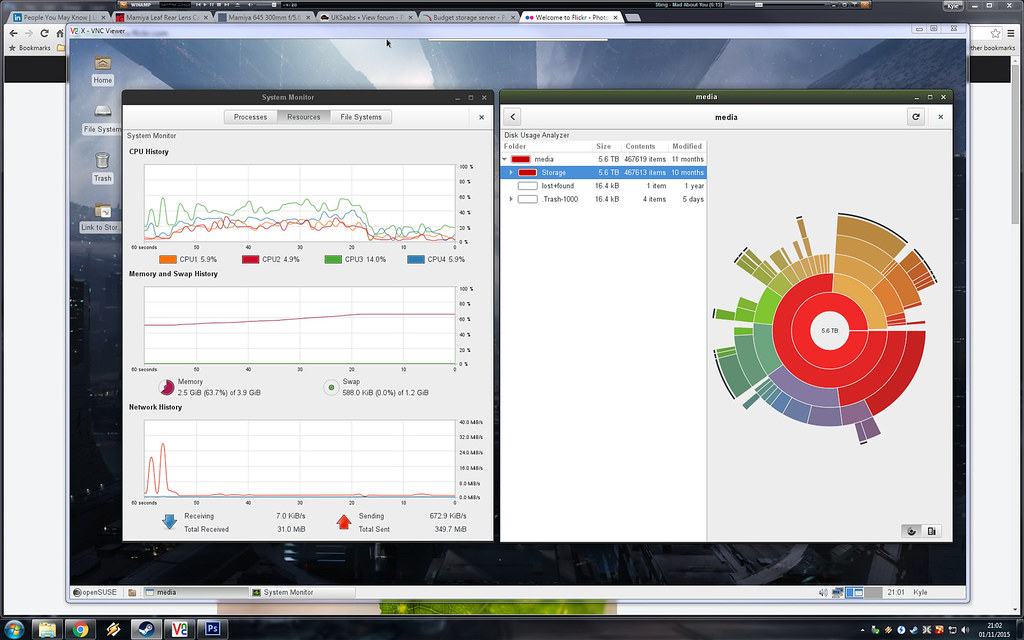
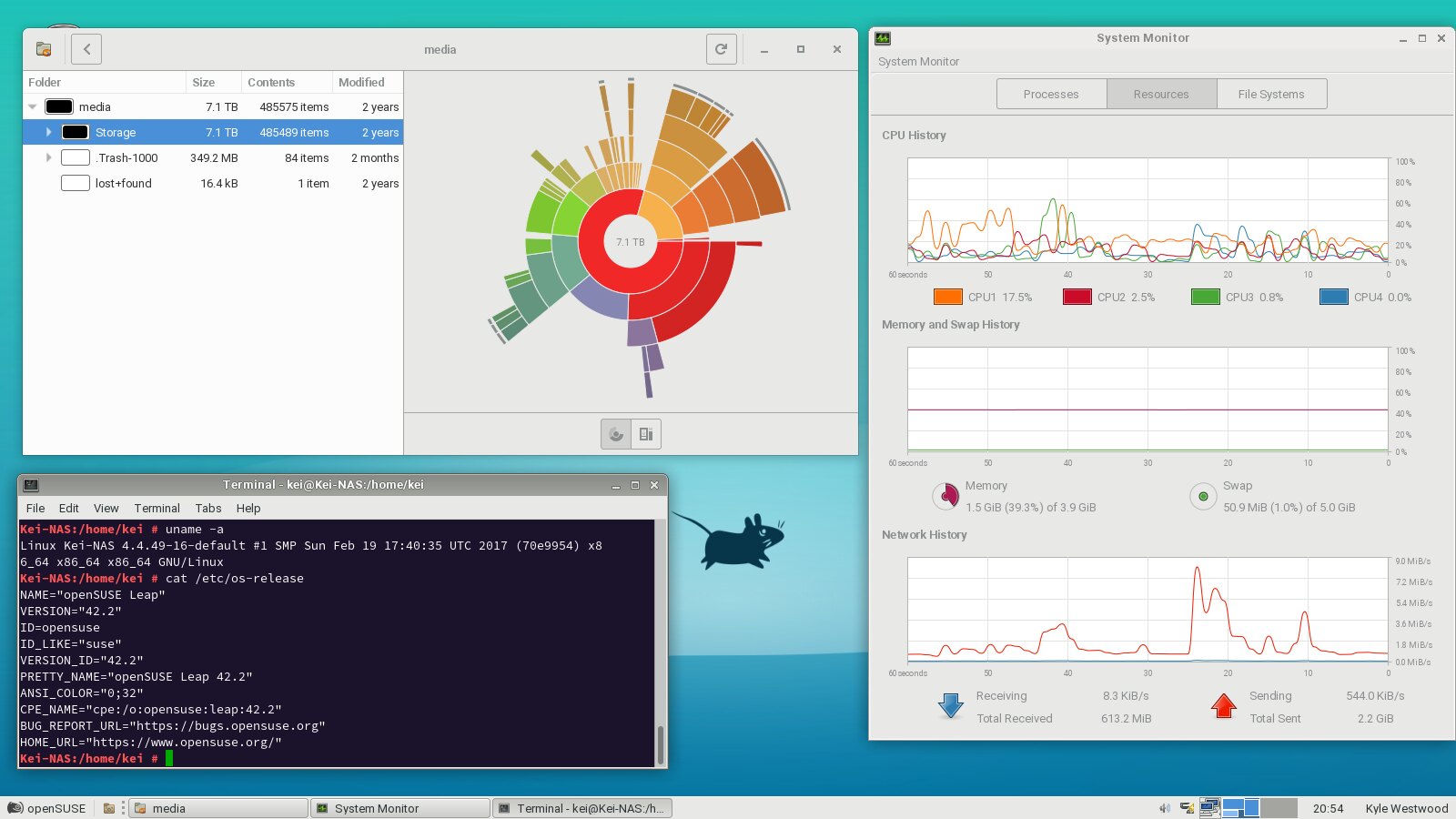
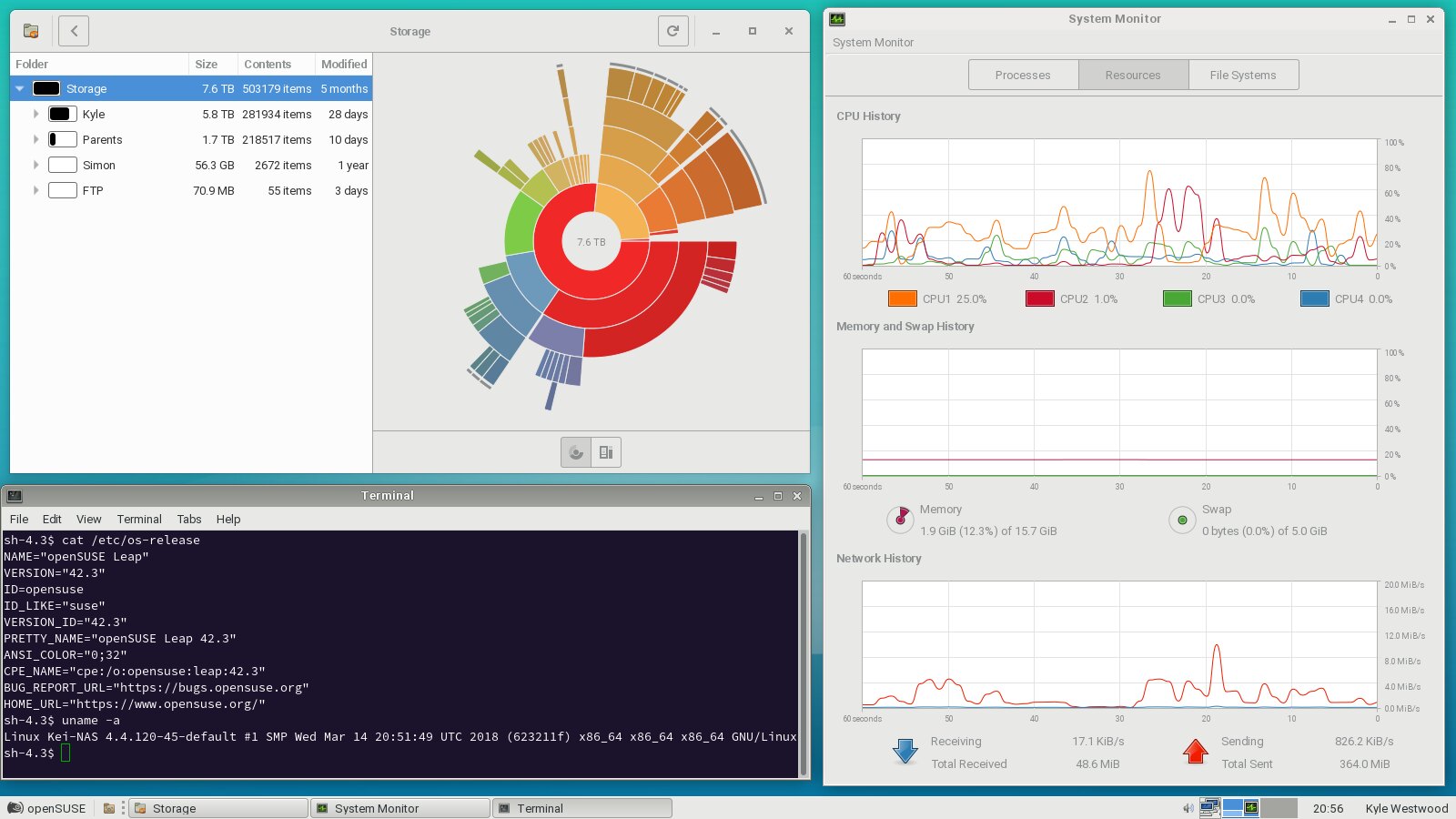
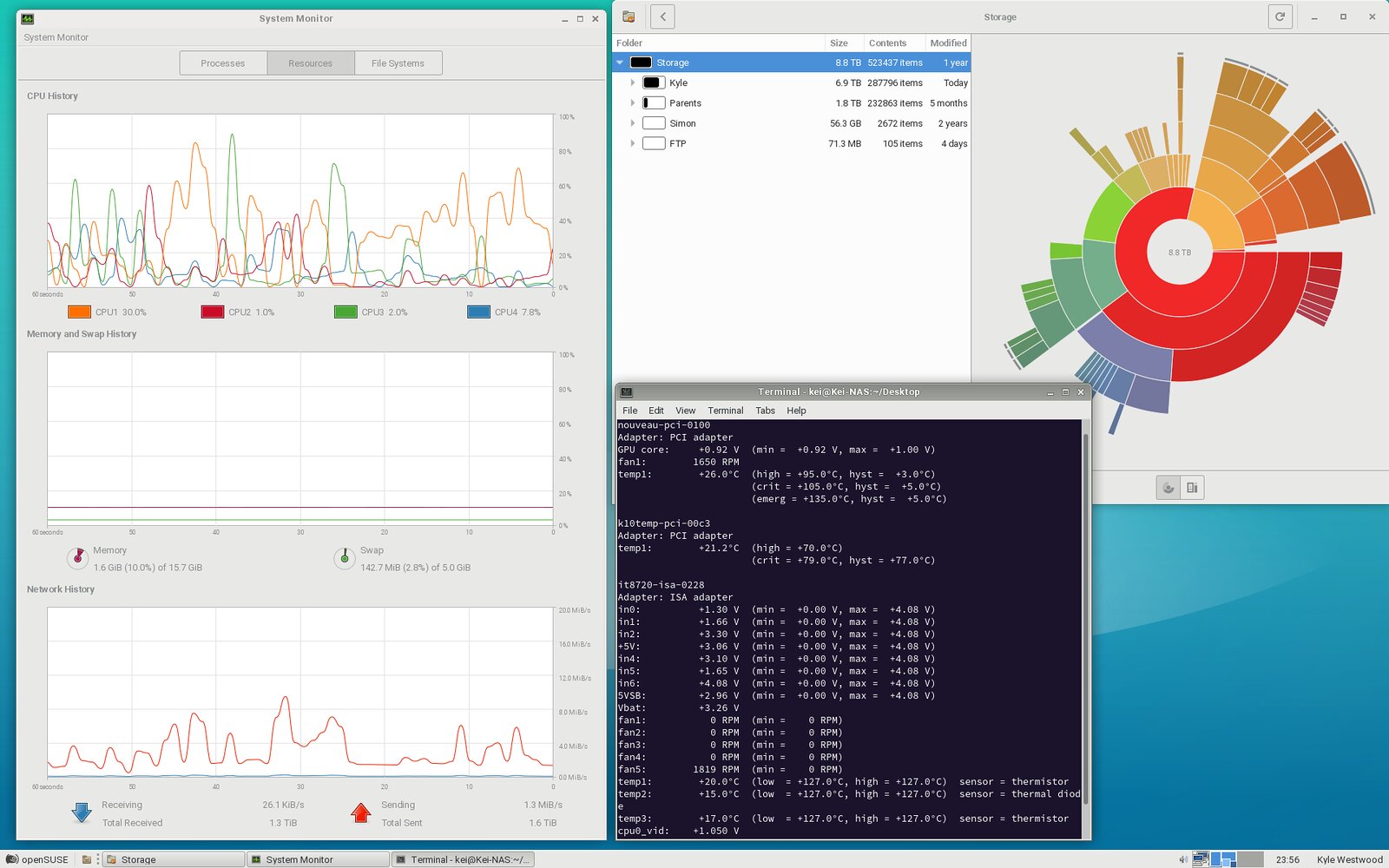
A full network rebuild has been performed as my old tp link 1043nd router has been requiring a prod every couple of days as it would just freeze up and stop all network traffic. I decided that i was up for a challenge and went with a cisco 1921/K9 ISR, an hp 1910-8G managed switch and a D-link DAP-2695 wireless access point. Complete and total overkill, I know, but I got them at a good price and being enterprise kit they ought to be reliable. (which was my main consideration) 5GHz wifi certainly is a lot quicker than 2.4 and the broadcast range from the d-link seems to travel slightly further too.


Having lived with it for just over a week, I can say that it has behaving well. (current PPPoE session has been up for 4 days so far, which is better than the tp link would usually manage) I certainly get better performance from it too. Very pleased there. (used to get low-mid 74 down and high 17- low 18 up, ping is about the same)

Config wise, it took me about 4 hours to configure the router sufficiently that i could access the internet. It took me a few days more and some assistance of the helpful network gurus to sort out the necessary static nat and access lists to get the server to be accessible from the outside for ftp, ssh and teamspeak. Still not sure on steam games as I don't do multiplayer very often. I'm not sure if I've covered all bases on the deny list but I'm hopeful that it's close.
The basic config for running with a bt infinity vdsl2 modem for those that are interested.


Having lived with it for just over a week, I can say that it has behaving well. (current PPPoE session has been up for 4 days so far, which is better than the tp link would usually manage) I certainly get better performance from it too. Very pleased there. (used to get low-mid 74 down and high 17- low 18 up, ping is about the same)

Config wise, it took me about 4 hours to configure the router sufficiently that i could access the internet. It took me a few days more and some assistance of the helpful network gurus to sort out the necessary static nat and access lists to get the server to be accessible from the outside for ftp, ssh and teamspeak. Still not sure on steam games as I don't do multiplayer very often. I'm not sure if I've covered all bases on the deny list but I'm hopeful that it's close.
The basic config for running with a bt infinity vdsl2 modem for those that are interested.
Code:
!
! Last configuration change at 12:44:44 UTC Tue Nov 11 2014
version 15.2
service tcp-keepalives-in
service tcp-keepalives-out
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname Cisco-1921
!
boot-start-marker
warm-reboot
boot-end-marker
!
!
enable secret 5.
enable password 7
!
no aaa new-model
!
ip cef
!
!
!!!!!!DHCP server config
ip dhcp excluded-address 192.168.0.1
ip dhcp excluded-address 192.168.0.50 192.168.0.51
!
ip dhcp pool main_dhcp_pool
network 192.168.0.0 255.255.255.0
default-router 192.168.0.1
dns-server x.x.x.x
!
ip dhcp pool Kei-PC
host 192.168.0.2 255.255.255.0
client-identifier xxx
client-name Kei-PC
!
ip dhcp pool Humax
host 192.168.0.4 255.255.255.0
client-identifier xxx
client-name Humax
!
ip dhcp pool Kei-NAS
host 192.168.0.3 255.255.255.0
hardware-address xxx
client-name Kei-NAS
!
ip dhcp pool Server
host 192.168.0.100 255.255.255.0
hardware-address xxx
!
!
!
ip domain name WesNet
ip name-server 8.8.8.8
no ipv6 cef
multilink bundle-name authenticated
!
!
!
license udi pid CISCO1921/K9 sn xxx
!
!!!!!Archive every 7 days or on writing config
archive
path ftp:/xxx/Cisco-1921
write-memory
time-period 10080
!
!
!
!
!
!
interface Embedded-Service-Engine0/0
no ip address
shutdown
!
!
!!!!!! Note that Ge0/0 has no IP address
interface GigabitEthernet0/0
no ip address
ip tcp adjust-mss 1452
duplex auto
speed auto
pppoe enable group global
pppoe-client dial-pool-number 1
!
!
!!!!!! This is the LAN side
interface GigabitEthernet0/1
ip address 192.168.0.1 255.255.255.0
ip nat inside
ip virtual-reassembly in
ip tcp adjust-mss 1452
duplex auto
speed auto
no mop enabled
!
!!!!!! The ISP's given IP address will be configured via d1
interface Dialer1
ip address negotiated
ip access-group 101 in
no ip unreachables
ip mtu 1492
ip nat outside
ip virtual-reassembly in
encapsulation ppp
dialer pool 1
ppp chap hostname [email protected]
ppp chap password 7 xxx
ppp pap sent-username [email protected] password 7 xxx
!
ip forward-protocol nd
!
ip http server
no ip http secure-server
!
!!!!!! This is the dynamic PAT between Dialer1 (WAN) interface IP address
!!!!!! and local IP addresses within ACL 1
ip nat inside source list 1 interface Dialer1 overload
ip nat inside source static tcp 192.168.0.3 20 interface Dialer1 20
ip nat inside source static tcp 192.168.0.3 21 interface Dialer1 21
ip nat inside source static tcp 192.168.0.3 22 interface Dialer1 22
ip route 0.0.0.0 0.0.0.0 Dialer1
ip route 192.168.0.0 255.255.255.0 GigabitEthernet0/1
!
access-list 1 remark INTERNET-ACCESS
access-list 1 permit 192.168.0.0 0.0.0.255
!
access-list 101 remark DENY FAKE IPs
access-list 101 deny ip 192.168.0.0 0.0.255.255 any
access-list 101 deny ip 172.16.0.0 0.15.255.255 any
access-list 101 deny ip 10.0.0.0 0.255.255.255 any
access-list 101 deny ip 127.0.0.0 0.255.255.255 any
access-list 101 deny ip 255.0.0.0 0.255.255.255 any
access-list 101 deny ip 248.0.0.0 7.255.255.255 any
access-list 101 deny ip 224.0.0.0 7.255.255.255 any
!
access-list 101 remark DENY SPOOFING IPs
access-list 101 deny ip host 0.0.0.0 any
access-list 101 deny ip host 255.255.255.255 any
!
access-list 101 remark DENY VULNERABLE PORTS
access-list 101 deny tcp any any range 135 139 log-input
access-list 101 deny udp any any range 135 139 log-input
access-list 101 deny tcp any any eq 2000 log-input
access-list 101 deny tcp any any eq 2001 log-input
access-list 101 deny tcp any any eq 6000 log-input
access-list 101 deny tcp any any eq 6001 log-input
access-list 101 deny tcp any any range 5900 5910 log-input
access-list 101 deny tcp any any range 5800 5810 log-input
access-list 101 deny tcp any any eq finger log-input
!
access-list 101 remark DENY TRACEROUTE OUTSIDE
access-list 101 deny udp any any range 33400 34400 log-input
!
access-list 101 remark ALLOW ACCESS FOR SERVER FTP & SSH
access-list 101 permit tcp any any eq 20
access-list 101 permit tcp any any eq 21
access-list 101 permit tcp any any eq 22
!
access-list 101 permit udp any any eq ntp
!
access-list 101 permit icmp any any net-unreachable
access-list 101 permit icmp any any host-unreachable
access-list 101 permit icmp any any port-unreachable
access-list 101 permit icmp any any packet-too-big
access-list 101 permit icmp any any administratively-prohibited
access-list 101 permit icmp any any source-quench
access-list 101 permit icmp any any ttl-exceeded
access-list 101 permit icmp any any echo-reply
access-list 101 deny icmp any any
access-list 101 permit tcp any any established
access-list 101 permit udp any any
!
!
!
!
snmp-server community WesNet RO
snmp-server enable traps entity-sensor threshold
!
control-plane
!
!
!
line con 0
line aux 0
line 2
no activation-character
no exec
transport preferred none
transport output pad telnet rlogin lapb-ta mop udptn v120 ssh
stopbits 1
line vty 0 4
password 7
login
transport input all
!
scheduler allocate 20000 1000
!
end
Last edited: