Been using a tp link TL-WR1043ND V1 since I moved to BT infinity a few years back. All told it's been great, but it is starting to get a bit unreliable, becoming completely inaccessible and stopping all network traffic. (a power cycle fixes it for a week or so) I've updated the firmware to the latest version and taken it to bits and replaced all the capacitors in the hope that it would solve the intermittent issue but nothing has worked so far.
I've been looking at all of the options out there and have to admit that they all seem a bit hit & miss going by the reviews. Mad as it may sound, I've been considering going all out and getting a dedicated router (cisco 1921) and separating the wireless using an access point connected via gigabit ethernet. I'd still be using the ECI vdsl2 modem as the HWIC cards for the cisco don't come cheap. I also realise that it will need configuring which isn't anywhere near as simple as a web interface.
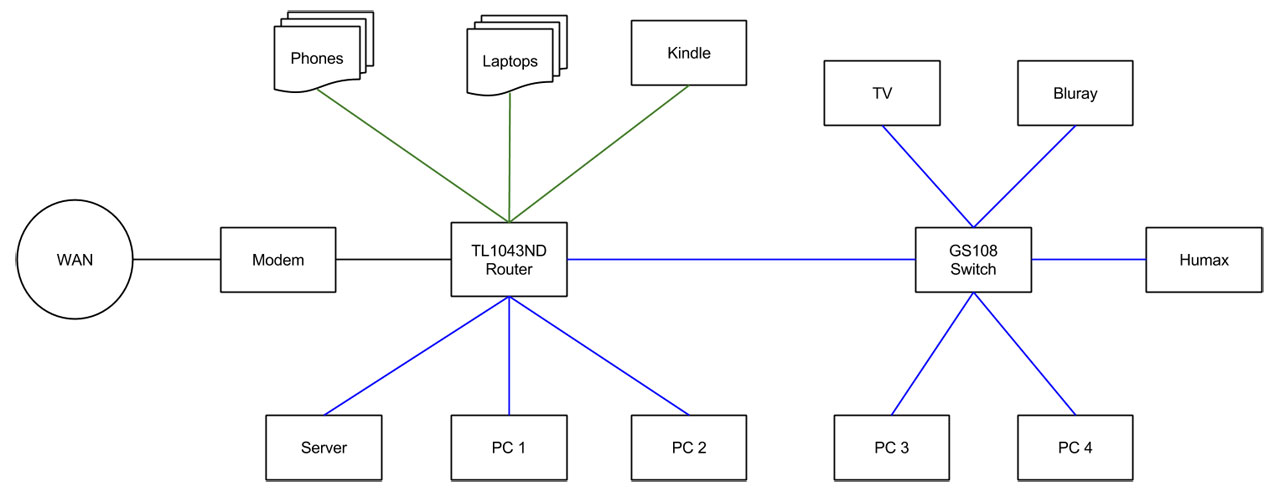
This is the current layout of our home network. Blue is cabled ethernet, green is wifi.
This was the idea I'd had for using the cisco router. I've been looking at the D-Link DAP-2695 as the access point and using a pair of unmanaged 8 port switches.

Anyone got any ideas. Like whether my idea really is as nuts as I think, or whether I can get something that will be reliable without needing perpetual firmware updates. The only requirements that i have are:-
For wifi, I merely need it to cover the house, which the current TP link just manages. Speed on wifi isn't important provided i get sufficient bandwidth for normal web browsing.
I've been looking at all of the options out there and have to admit that they all seem a bit hit & miss going by the reviews. Mad as it may sound, I've been considering going all out and getting a dedicated router (cisco 1921) and separating the wireless using an access point connected via gigabit ethernet. I'd still be using the ECI vdsl2 modem as the HWIC cards for the cisco don't come cheap. I also realise that it will need configuring which isn't anywhere near as simple as a web interface.
This is the current layout of our home network. Blue is cabled ethernet, green is wifi.

This was the idea I'd had for using the cisco router. I've been looking at the D-Link DAP-2695 as the access point and using a pair of unmanaged 8 port switches.

Anyone got any ideas. Like whether my idea really is as nuts as I think, or whether I can get something that will be reliable without needing perpetual firmware updates. The only requirements that i have are:-
- Reliable
- Secure
- Port forwarding
- DHCP address reservation
For wifi, I merely need it to cover the house, which the current TP link just manages. Speed on wifi isn't important provided i get sufficient bandwidth for normal web browsing.
Last edited:



