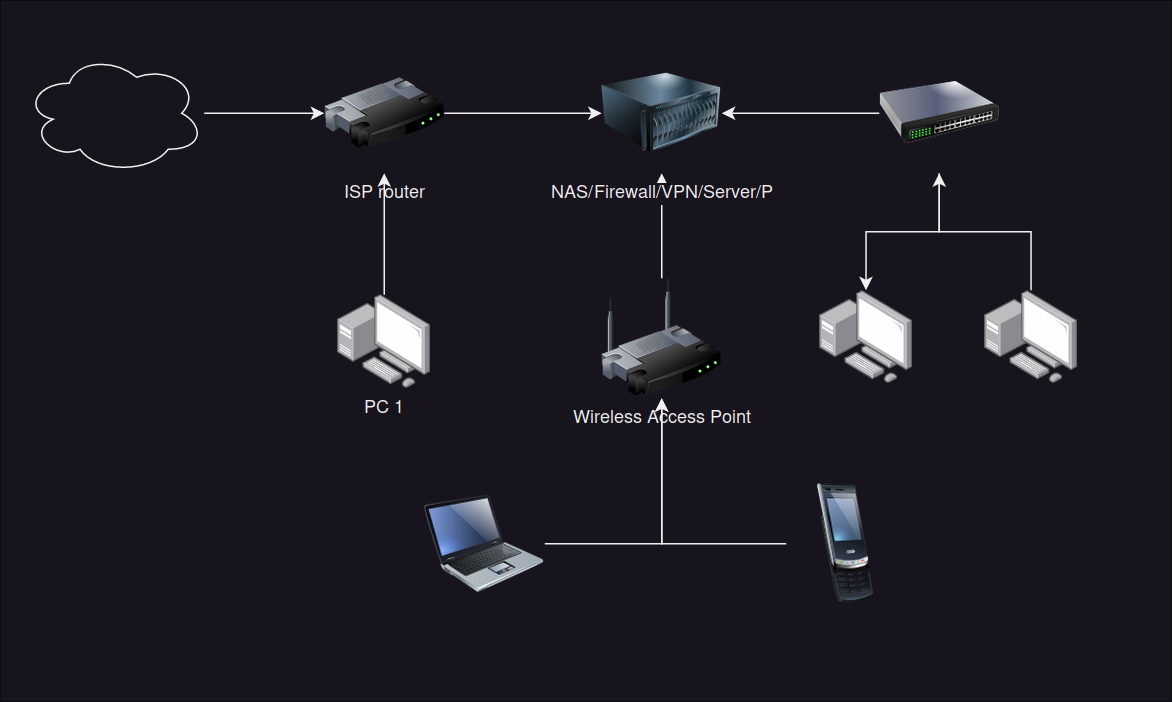
This may be really simple but before I buy anything here's an overview of my network setup:
 images upload
images upload
I have a single cat6a ethernet cable from the ISP router to my server which acts as a firewall, nas and VPN.
The idea was that everything would go through this. Unfortunately, I had FTTP installed and they couldn't practically install box on the wall on the side of the house I wanted them to which means I have this setup. It's fine but PC1 connects directly through the ISP router to access the internet, it's not behind the firewall and I don't want to open my NAS up to connections from the ISP router end. I'd run another cable but unfortunately I've just had the floors redone as I thought I'd got all the network infrastructure sorted.
Is it possible to have the equivalent of two cables so that the traffic for PC1 follows the orange arrow in this diagram?
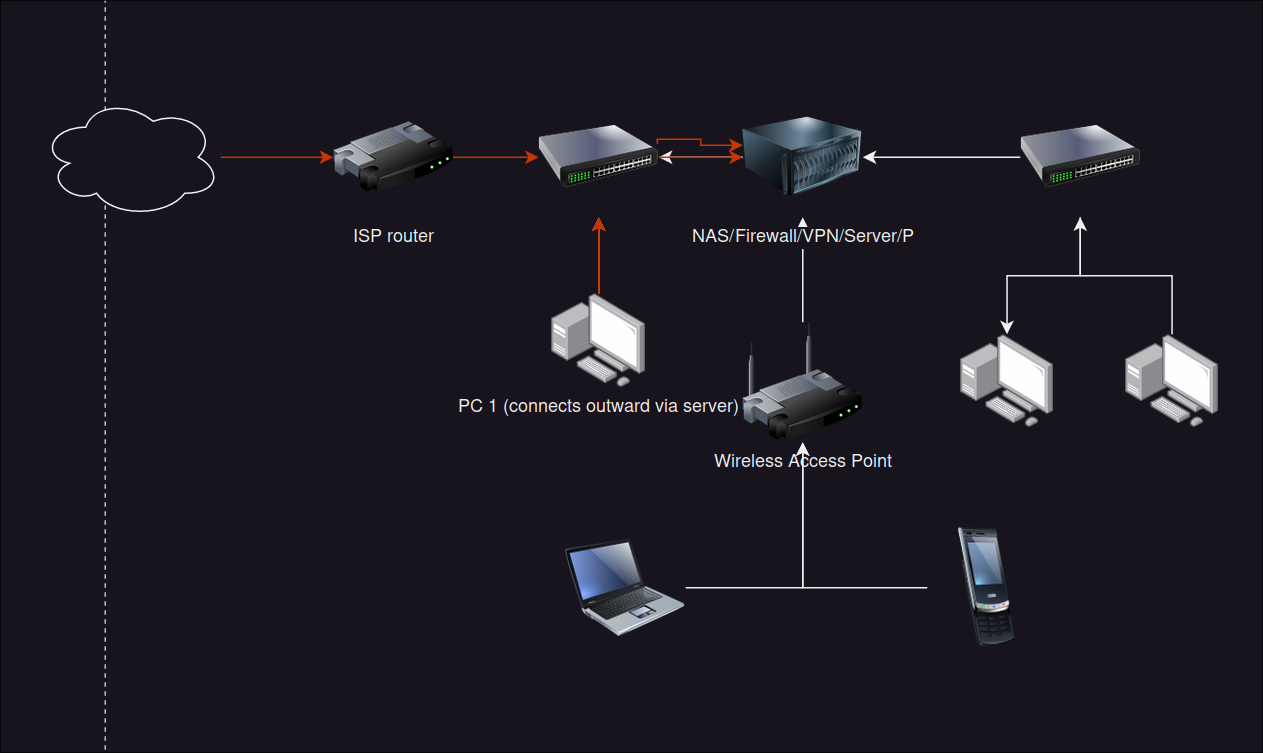
I obviously need some additional hardware here. Can I do this with a cheap gigabit switch or do I need something more fancy? I want to be able to block all connections from the ISP router to the server and outbound connections from PC1 should go via the VPN running on the server. Using WiFI on PC1 would solve the problem but I'd rather not do that as it's a tiny HTPC and would need an external adapter.
Thanks for any advice!
 images upload
images uploadI have a single cat6a ethernet cable from the ISP router to my server which acts as a firewall, nas and VPN.
The idea was that everything would go through this. Unfortunately, I had FTTP installed and they couldn't practically install box on the wall on the side of the house I wanted them to which means I have this setup. It's fine but PC1 connects directly through the ISP router to access the internet, it's not behind the firewall and I don't want to open my NAS up to connections from the ISP router end. I'd run another cable but unfortunately I've just had the floors redone as I thought I'd got all the network infrastructure sorted.
Is it possible to have the equivalent of two cables so that the traffic for PC1 follows the orange arrow in this diagram?

I obviously need some additional hardware here. Can I do this with a cheap gigabit switch or do I need something more fancy? I want to be able to block all connections from the ISP router to the server and outbound connections from PC1 should go via the VPN running on the server. Using WiFI on PC1 would solve the problem but I'd rather not do that as it's a tiny HTPC and would need an external adapter.
Thanks for any advice!
Last edited:


