You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
How to protect from ransomware?
- Thread starter Amaede
- Start date
More options
Thread starter's postsSoldato
- Joined
- 17 Oct 2005
- Posts
- 6,243
- Location
- North of Watford Gap
I can't speak for OneDrive, but if you use the Dropbox sync program on Windows it will just encrypt the files as normal and Dropbox, seeing a change, would upload them. Dropbox gives you 30 days to restore files though, so in theory you would be able to recover any lost files.Can this 'worm' affect data on drives such as Dropbox or OneDrive?
Andi.
The MS patching mechanism do not make it easy for the consumer (non enterprise) to just make security patches for win7/win10In what way? They released patches prior to the attacks
The patching mechanism is notoriously unreliable (folks machines lock-up) so I cannot, but empathise, with folks, when they disable/defer updates.
Since Win10, where users (insiders) have been 'employed' for testing software I think this has corresponded to a down-turn in MS app and security
software quality, however, I do not know if Apple, say, spend more on these aspects of ecosystem.
The SMB weakness was patched, yes (and XP), but, the other recent malware scanner/zero day exploit was identified by a 3rd party, not MS, so - another s/w quality delinquency.
(I think people would pay MS an annual maintenance fee, like many do for 3rd party A/V if the s/w quality was improved. )
Problem is a bit like facebook, where FB currently try and abdicate responsibility to the economic/social cost of some of the content their
'platform' propagates (eg isis), but they need to accept some social responsibility, as indeed MS do... but hopefully legislation will catch up, or indeed a responsible competitor arises. (ministry of Truth)
It will be interesting to see economic cost to UK NHS for last week's attacks - 200M per day running costs.
Soldato
- Joined
- 17 Oct 2005
- Posts
- 6,243
- Location
- North of Watford Gap
The vast majority of users can't disable or defer updates. As I'm sure you know Pro users can defer major updates (such as Creators Edition), as can Enterprise and Education, but these are policies set by the organisation. They cannot defer standard updates, only not push them out through WSUS/SCCM, and this will be a conscious effort on the part of an admin who, if they were attacked, is now going to have to explain to his superiors exactly why he shouldn't be fired on the spot for gross negligence.The MS patching mechanism do not make it easy for the consumer (non enterprise) to just make security patches for win7/win10
The patching mechanism is notoriously unreliable (folks machines lock-up) so I cannot, but empathise, with folks, when they disable/defer updates.
That you want that decision to fall at Microsoft's feet is baffling.
Microsoft aren't responsible for organisations refusing to apply the March patch, but if people are going to hold Microsoft accountable then the only outcome will be forced upgrades and updates for home and enterprise/education users.
March!
It was funny watching Jayne Secker starting to getting angry on Sky News 30 minutes ago about it and asking the security guy if he'll step down.
Yes, let's get rid of those who understand with those that don't.March!
It was funny watching Jayne Secker starting to getting angry on Sky News 30 minutes ago about it and asking the security guy if he'll step down.
 Who was it who ignored warnings? Those that understand or those that don't?
Who was it who ignored warnings? Those that understand or those that don't?Andi.
was there a specific doc that says it does not get admin privileges like this-Set up your backups so they go to a location that your default user only has read-only access to. Also set any shared media folders to read-only.
http://www.securityweek.com/erebus-ransomware-bypasses-uac-privilege-elevation ransomware. ?
I was unable to find that kind of info.
Yeah need to ensure any write protection itself isn't vulnerable - ideally a medium like good old CD/DVD-R or a memory card or drive with a physical write protection switch. Linux's permissions are also fairly secure at the moment - but there is the possibility of user accounts being compensable on certain NAS boxes even if they use Linux based stuff themselves.
Rotated offline USB drives should be sufficient - if really worried restore them via an Android or Linux based device.
Rotated offline USB drives should be sufficient - if really worried restore them via an Android or Linux based device.
Soldato
- Joined
- 28 Sep 2014
- Posts
- 3,761
- Location
- Scotland
Symantec has more information about WannaCry ransomware:
https://www.symantec.com/connect/blogs/what-you-need-know-about-wannacry-ransomware
I never opened attached compressed files, phishing links from unknown address and sources in emails. 2 years ago I had 1 email looked genuine that had attached compressed rar file and I am not so very sure I can trust it but I never opened it outside sandbox so I moved rar file into Virtualbox running Windows 8.1 then installed Norton Security trial and ran LiveUpdate to get latest updates. I tried decompressed rar file but both Norton Security ran on host OS and VM detected it as ransomware and blocked it then I deleted email from host OS.
I recommend you to install anti-virus security software like Norton Security which offer full protection from ransomwares that basic Windows Defender had no protection from ransomwares and also Norton Security's Safe Web offer you protection from rogue websites and links detected infected with malware, botnet, phishing and ransomware. If you click a link to a website infected with malware and ransomware then you will get a Norton warning notice warned you that website is not safe to visit contained harmful malware programs.
I also moved downloaded files, critical files, emails, videos and pictures I not used for months or years to offline hard drive. I recommend you to do the same so I got nothing to worry about ransomware in future, I always installed Norton Security first thing after booted cleaned installed Windows.
https://www.symantec.com/connect/blogs/what-you-need-know-about-wannacry-ransomware
I never opened attached compressed files, phishing links from unknown address and sources in emails. 2 years ago I had 1 email looked genuine that had attached compressed rar file and I am not so very sure I can trust it but I never opened it outside sandbox so I moved rar file into Virtualbox running Windows 8.1 then installed Norton Security trial and ran LiveUpdate to get latest updates. I tried decompressed rar file but both Norton Security ran on host OS and VM detected it as ransomware and blocked it then I deleted email from host OS.
I recommend you to install anti-virus security software like Norton Security which offer full protection from ransomwares that basic Windows Defender had no protection from ransomwares and also Norton Security's Safe Web offer you protection from rogue websites and links detected infected with malware, botnet, phishing and ransomware. If you click a link to a website infected with malware and ransomware then you will get a Norton warning notice warned you that website is not safe to visit contained harmful malware programs.
I also moved downloaded files, critical files, emails, videos and pictures I not used for months or years to offline hard drive. I recommend you to do the same so I got nothing to worry about ransomware in future, I always installed Norton Security first thing after booted cleaned installed Windows.
I mean shared folders on a NAS drive, should have been more specific.was there a specific doc that says it does not get admin privileges like this
http://www.securityweek.com/erebus-ransomware-bypasses-uac-privilege-elevation ransomware. ?
I was unable to find that kind of info.
Associate
- Joined
- 31 Oct 2012
- Posts
- 2,243
- Location
- Edinburgh
If you're a bit paranoid like me then run your daily account as a non-admin user (more robust than UAC as standard UAC-bypasses don't do anything to you). As well as all the things already suggested about backups, updates and not clicking dodgy links etc. Simple things like making the admin account have a unique name actually helps slightly too.
Edit: Also plenty stuff can be done from VMs where there is less danger of a system-wide problem, mostly just the VM getting messed up.
Edit: Also plenty stuff can be done from VMs where there is less danger of a system-wide problem, mostly just the VM getting messed up.
Last edited:
If you're a bit paranoid like me then run your daily account as a non-admin user. As well as all the things already suggested about backups, updates and not clicking dodgy links etc.
Almost pointless on Windows even 10, though still a sound strategy in Linux - despite what some claim there are vulnerabilities that allow malware to go straight through UAC on Windows i.e. vulnerabilities in some signed device drivers - it'll stop less sophisticated malware but little against more serious stuff.
EDIT: Though no harm doing it if it doesn't impact on your day to day usage and might save you from a less sophisticated attack.
Norton Security
Norton in my experience has generally severely slowed down a system and/or had other limitations - one thing if you are mostly doing a bit of web browsing and watching videos but for someone that is closer to that of a power user it will have significant trade offs for the security it provides.
Last edited:
Symantec has more information about WannaCry ransomware:
https://www.symantec.com/connect/blogs/what-you-need-know-about-wannacry-ransomware
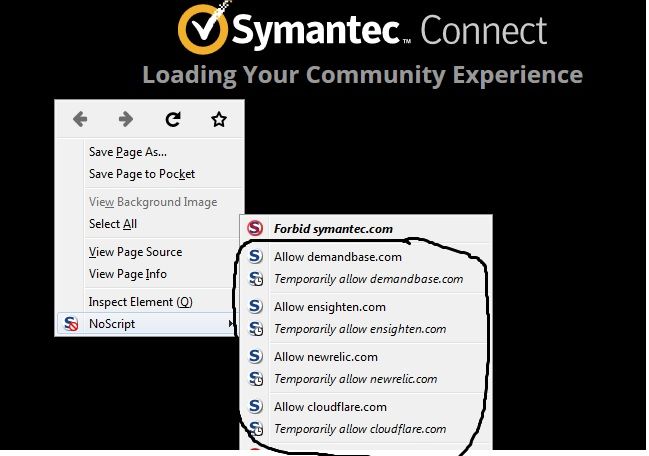
no this is paranoia ? have you seen how many toolkits/3rd parties the symantec web site relies on -
if one of those gets taken so does symantec ? (courtesy of FF noscript)
I expect A/V sites to be single source, not a blend.
Norton in my experience has generally severely slowed down a system and/or had other limitations - one thing if you are mostly doing a bit of web browsing and watching videos but for someone that is closer to that of a power user it will have significant trade offs for the security it provides.
I certainly haven't experienced slowdown...
no this is paranoia ? have you seen how many toolkits/3rd parties the symantec web site relies on -
if one of those gets taken so does symantec ? (courtesy of FF noscript)
I expect A/V sites to be single source, not a blend.
That is nothing compared to some sites these day
 I've seen over 100 entries in noscript for a single simple site before. Its not surprising people run ad blockers heh. Very bad for security - its how the Guru3D ad compromise worked a few years back which got a lot of people probably many who didn't even realise.
I've seen over 100 entries in noscript for a single simple site before. Its not surprising people run ad blockers heh. Very bad for security - its how the Guru3D ad compromise worked a few years back which got a lot of people probably many who didn't even realise.I've been virus free for a long time now. Although my modem had the DNS changed a few years ago.
But all this has made me think about security. I've always run AVG free. But I'm currently running Kaspersky total security. Free 30 day trial. (bank with barclays so could also get a big discount) on a scale of 1-100 how paranoid am I being that its run by a Russian...
But all this has made me think about security. I've always run AVG free. But I'm currently running Kaspersky total security. Free 30 day trial. (bank with barclays so could also get a big discount) on a scale of 1-100 how paranoid am I being that its run by a Russian...

