You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Self hosting bitwarden
- Thread starter chili
- Start date
More options
Thread starter's postsI've been self-hosting Bitwarden for years now and don't regret it. I run it in Docker on a Raspberry Pi 4. I actually run Vaultwarden, which is a Rust-based back-end server for BitWarden and is much much lighter on resources and much quicker. Additionally, all the premium features are unlocked in Vaultwarden (organisations, family stuff etc.).
it's easy enough to do but I wouldn't make it (or anything really) internet facing. I have mine accessible over my local network and sync stuff when I'm home.
The vault is still accessible on my phone/laptop outside my local network but I don't have to worry about the security implications of anyone in the world being able to connect to it. The only pain point is that it's read only when I'm not at home, in the odd case I need to register an account when I'm not at home I have a secure temporary password in my vault that I use, then change it when I'm home.
(and if I try to log in to something later and it's not in my vault, I know that it must be the temporary password)
The vault is still accessible on my phone/laptop outside my local network but I don't have to worry about the security implications of anyone in the world being able to connect to it. The only pain point is that it's read only when I'm not at home, in the odd case I need to register an account when I'm not at home I have a secure temporary password in my vault that I use, then change it when I'm home.
(and if I try to log in to something later and it's not in my vault, I know that it must be the temporary password)
it's easy enough to do but I wouldn't make it (or anything really) internet facing. I have mine accessible over my local network and sync stuff when I'm home.
The vault is still accessible on my phone/laptop outside my local network but I don't have to worry about the security implications of anyone in the world being able to connect to it. The only pain point is that it's read only when I'm not at home, in the odd case I need to register an account when I'm not at home I have a secure temporary password in my vault that I use, then change it when I'm home.
(and if I try to log in to something later and it's not in my vault, I know that it must be the temporary password)
A free Tailscale account could solve this
Their MagicDNS product is effectively a reverse proxy, right? So presumably you have to install something on the server that's running Bitwarden/Vaultwarden so it can talk to Tailscale's service. I would argue that still opens you up in a way - you are relying on their service being secure and not exposing what you run as well as protecting you from potential threats. You also have to trust that whatever needs to run on your server is free of security issues as it is after all a tunnel into your server. Unless I misunderstand the MagicDNS service?A free Tailscale account could solve this
Last edited:
Tailscale is essentially a Wireguard VPN with a very fancy management layer. So the actual device to device connections are as secure as any other Wireguard implementation (ie. extremely), but there is an argument that their management layer could be compromised or misconfigured in such a way that leaves your supposedly private network at risk - in a way that a DIY Wireguard deployment may not.Their MagicDNS product is effectively a reverse proxy, right? So presumably you have to install something on the server that's running Bitwarden/Vaultwarden so it can talk to Tailscale's service. I would argue that still opens you up in a way - you are relying on their service being secure and not exposing what you run as well as protecting you from potential threats. You also have to trust that whatever needs to run on your server is free of security issues as it is after all a tunnel into your server. Unless I misunderstand the MagicDNS service?
It's your typical convenience / usability / security trade off.
Their MagicDNS product is effectively a reverse proxy, right? So presumably you have to install something on the server that's running Bitwarden/Vaultwarden so it can talk to Tailscale's service. I would argue that still opens you up in a way - you are relying on their service being secure and not exposing what you run as well as protecting you from potential threats. You also have to trust that whatever needs to run on your server is free of security issues as it is after all a tunnel into your server. Unless I misunderstand the MagicDNS service?
Sorry missed this until just now. The explanation above was spot on - secure wireguard VPN but with an easy to use management layer
The magic DNS service from what I’ve seen just automatically resolves the hostnames of your Tailscale connected clients
Personally I’m happy with the security of Tailscale for my specific use cases but if you wanted to go further you could run the Tailscale client on a VM that acts as an exit node towards your network then do additional firewalling
Thank youSorry missed this until just now. The explanation above was spot on - secure wireguard VPN but with an easy to use management layer
The magic DNS service from what I’ve seen just automatically resolves the hostnames of your Tailscale connected clients
Personally I’m happy with the security of Tailscale for my specific use cases but if you wanted to go further you could run the Tailscale client on a VM that acts as an exit node towards your network then do additional firewalling
 Was more curious than anything - I have mine running an nginx proxy on a Pi!
Was more curious than anything - I have mine running an nginx proxy on a Pi!I've been self-hosting Bitwarden for years now and don't regret it. I run it in Docker on a Raspberry Pi 4. I actually run Vaultwarden, which is a Rust-based back-end server for BitWarden and is much much lighter on resources and much quicker. Additionally, all the premium features are unlocked in Vaultwarden (organisations, family stuff etc.).
Same here, Vaultwarden is flawless. It's especially good since they booted the old Rocket and websockets palaver on dedicated ports. Now everything just runs nicely behind a reverse proxy on :443.
 OP, definitely read the Vaultwarden Wiki, and make sure you thoroughly understand everything - including daily backups offsite.
OP, definitely read the Vaultwarden Wiki, and make sure you thoroughly understand everything - including daily backups offsite.I’m currently trying this but had issues with nginx proxy manager, seems to be flaky or I’m not using it right. Going to try Traefik, anyone else using that?
My plan is to wireguard VPN into my router and then through firewall to reverse proxy docker on server. I have a new domain on Cloudflare and a static IP, I was hoping to use that also to obtain SSL certs for local use. Would that work? Can’t seem to see a guide for exactly that setup. I’m using Pihole internally for DNS as well.
My plan is to wireguard VPN into my router and then through firewall to reverse proxy docker on server. I have a new domain on Cloudflare and a static IP, I was hoping to use that also to obtain SSL certs for local use. Would that work? Can’t seem to see a guide for exactly that setup. I’m using Pihole internally for DNS as well.
For NPM:I’m currently trying this but had issues with nginx proxy manager, seems to be flaky or I’m not using it right. Going to try Traefik, anyone else using that?
My plan is to wireguard VPN into my router and then through firewall to reverse proxy docker on server. I have a new domain on Cloudflare and a static IP, I was hoping to use that also to obtain SSL certs for local use. Would that work? Can’t seem to see a guide for exactly that setup. I’m using Pihole internally for DNS as well.
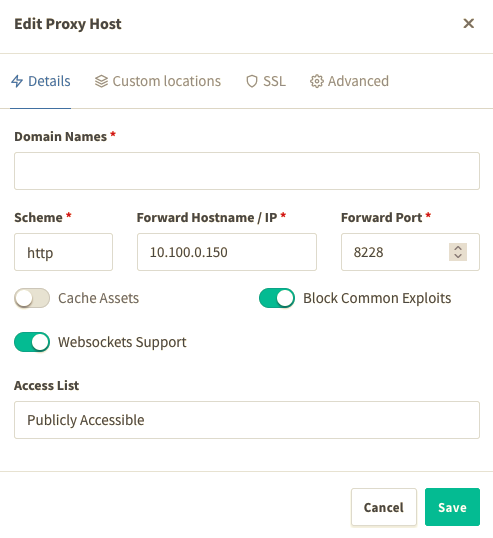
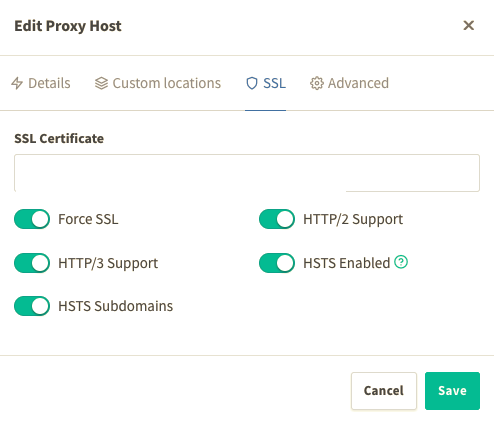
Then in Advanced > Custom nginx config:
Code:
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-Protocol $scheme;
proxy_set_header X-Forwarded-Host $http_host;
add_header X-Frame-Options "SAMEORIGIN";
add_header X-XSS-Protection "0";
add_header X-Content-Type-Options "nosniff";
add_header X-Robots-Tag "noindex, nofollow";
location /admin {
return 404;
}I have selfhosted it before, vaultwarden docker, with traefik and authelia for secure external access.
In the end I have gone for the family subscription as it is such a core service I wanted to remove the faff.
It worked fine for me, and also external access, but I never got it working quite right when accessing from different VLANs at home, entirely networking related rather than bitwarden/vaultwarden which works perfectly!
In the end I have gone for the family subscription as it is such a core service I wanted to remove the faff.
It worked fine for me, and also external access, but I never got it working quite right when accessing from different VLANs at home, entirely networking related rather than bitwarden/vaultwarden which works perfectly!
I got it working in the end by using traefik and the vaultwarden docker, just needed all the tags for traefik setup properly.
It’s self hosted but not available externally. I did have a VPN server that would allow me to get to it, but that’s not currently running. Not really an issue, it just syncs once I’m back home.
It’s self hosted but not available externally. I did have a VPN server that would allow me to get to it, but that’s not currently running. Not really an issue, it just syncs once I’m back home.

