I was with you right up until the C2558, between Intel screwing up the production so they will die prematurely and the Asrock bios write bug, a lot of people got burnt on Avoton, at least you went Supermicro. The point you raise on ASUS updates is an interesting one, i'd imagine the FTC required patching of all historic products affected, given the likely settlement was large and will have had the threat of additional future penalties made clear, i'd imagine they'll keep maintaining the code base from a security perspective until they can justify not doing so.
Asus on the ball? They're still debating if it's flat or not.
Have a closer look at the later pages of the AC68 thread (also includes the N66 etc.) and the hate directed towards the product/ASUS, Andy_82 is correct, ASUS promised to resolve the issue then just ghosted users after stringing them along for years. Asus got nailed by the FTC in 2016 over it's fundamental failure to patch gaping security holes over a long period of time and then not notifying customers that the updates existed (the whole update mechanism was broken/easily attacked via MiM style attacks as it operated over http so could be tricked into downloading anything). Generally you don't agree to a large fine and 20 years of forced external auditing on a bi-anual basis, that said ASUS's patch history previously ran over two years, so perhaps this is progress? The FCC (not the FTC) fined ASUS $240K in 2014 for faking test data to gain certifications on numerous devices over a long period, Netgear also sued them over this and settled out of court.
https://www.ftc.gov/system/files/documents/cases/160222asuscmpt.pdf
https://www.fcc.gov/document/asustek-pay-240k-resolve-equipment-marketing-investigations
I'd personally suggest that any single one of those is significant enough to ask some serious questions of ASUS and reconsider if you'd really recommend the product to others, all three of them combined with the other history makes it clear how ASUS feels about consumers and our security.


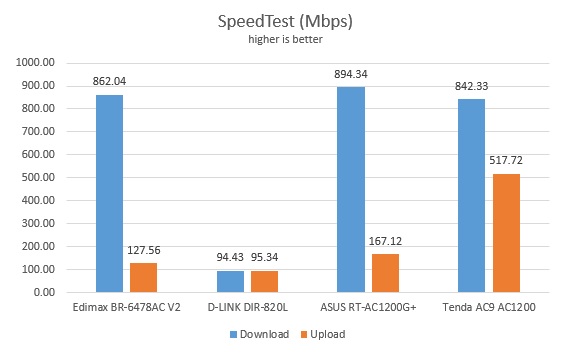
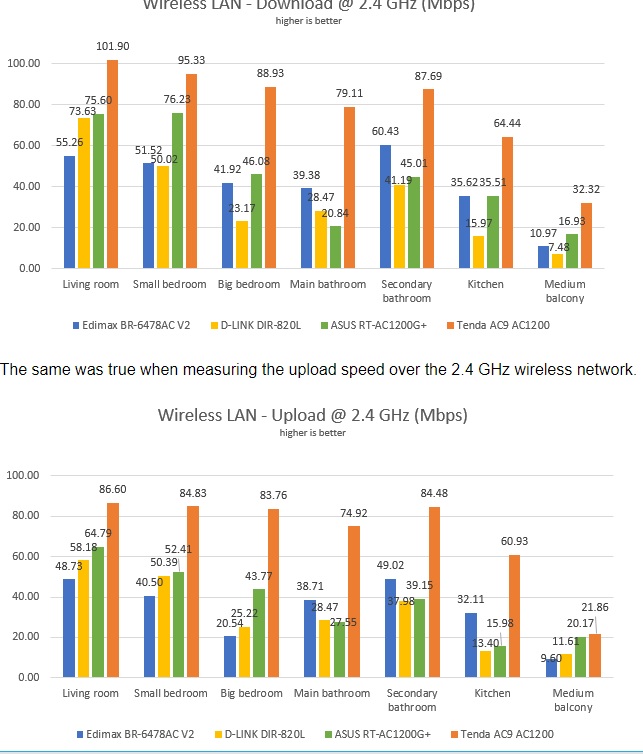
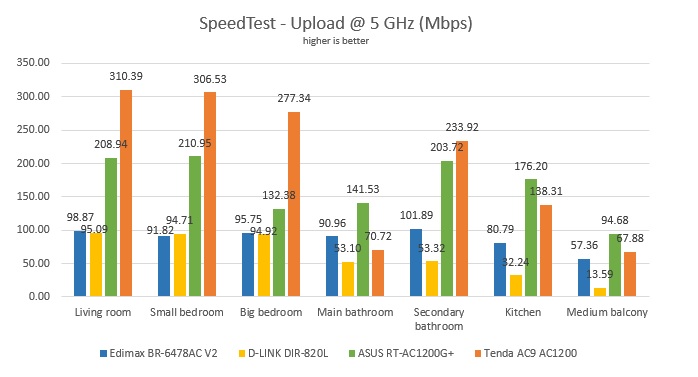
 Actually, I wouldn't recommend it to any of my close neighbours because it isn't in my interest to have a so good signal device close to mine. Might interfere.
Actually, I wouldn't recommend it to any of my close neighbours because it isn't in my interest to have a so good signal device close to mine. Might interfere.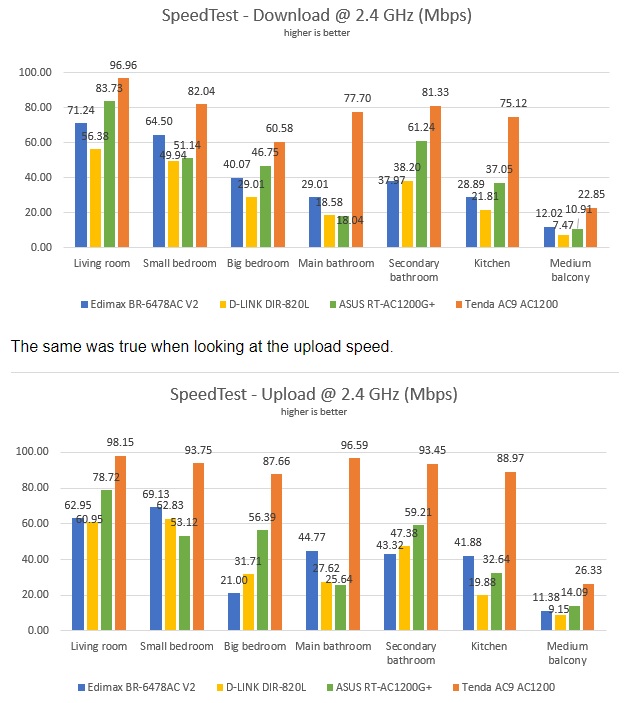
 free photo hosting
free photo hosting