I've often been asked why I have two Piholes. My answer is always the same in that it's for redundancy, in case one breaks. That doesn't take into account stupidity which is what happened a day or say ago.
I had two piholes, pihole-buster1 and pihole-buster2, the former running on a P4 and the latter on a Zero. I swapped the Zero for a Zero2 and it was just a case of moving the SD card over and it worked perfectly. I didn't expect that to work when going from a 4 to a Zero2W and I was right.
Rebuilding was easy enough, I called the new one pihole-bullseye1 and got it all set up nicely. I have various scripts running that copy files from 1 to 2 and if I need to make any changes on 1, they get replicated to 2 overnight.
Where I made a mistake was by mistyping a - for an = in /etc/dnsmasq.d/02-pihole-dhcp.conf. I didn't restart the service after editing the file on pihole-bullseye1 so it didn't show up as a problem. At 01:00 in the morning, the file was replicated over to pihole-buster2 and the FTL service restarted. Because of the typo, the services I restart failed to restart leaving it effectively down.
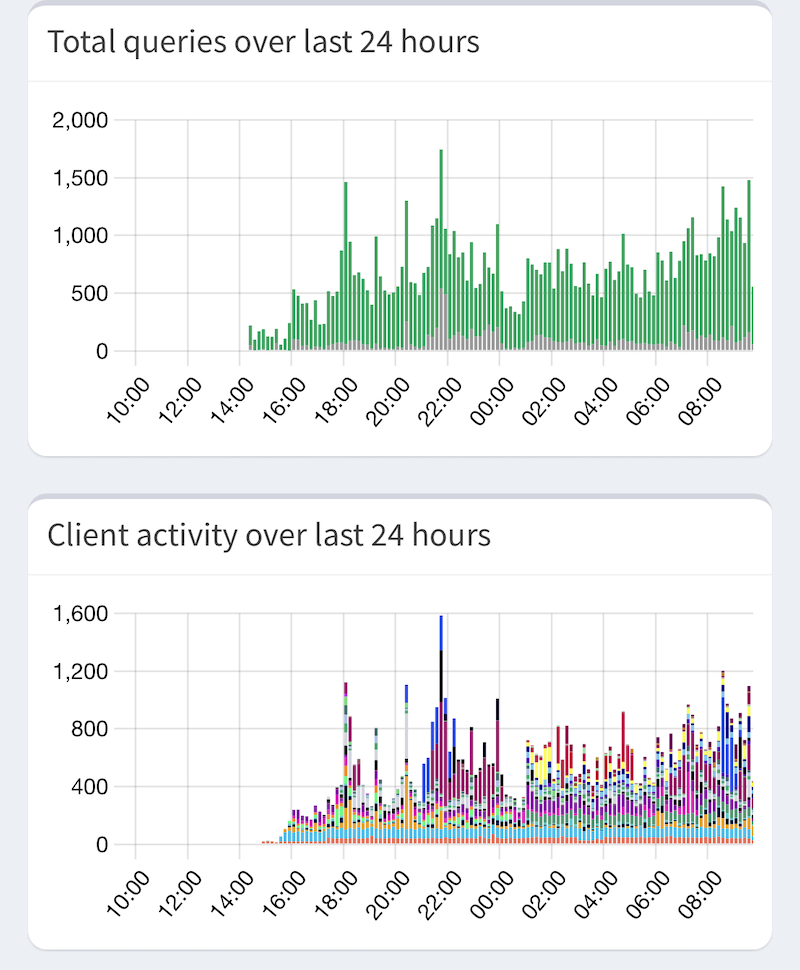
You see where it all went a bit rubbish and then where I recovered it the next morning.

The new one did a splendid job though and everything continued working. This was a proper trial by fire, you can see I only got it online a few hours before.
"So @Feek, how do you have two Piholes working together?" I hear you ask.
It's pretty straightforward although it sounds confusing as I type it.
My Piholes run DHCP as well as DNS so they're each configured slightly differently.
From the dashboard, go to Settings / DHCP
On the first Pihole, I have the DHCP server enabled and the range of IP addresses is set from 192.168.1.20 to 192.168.1.59
On the second Pihole, I also have the DHCP server enabled and the range of IP addresses is set from 192.168.1.60 to 192.168.1.100
That gives me a total of 80 available DHCP addresses in the pool. I have the lease time set to just 6 hours on both so there are always plenty of available leases.
The next thing I do is to edit /etc/dnsmasq.d/02-pihole-dhcp.conf and add an extra line.
The two Piholes are on 192.168.1.11 and 192.168.1.12
On the first Pihole, I add
dhcp-option=6,192.168.1.11,192.168.1.12
On the second Pihole, I add
dhcp-option=6,192.168.1.12,192.168.1.11
(then restart FTL/dns or just reboot the Pi)
That means that any device which DHCPs from the first Pihole will be given the first Pihole as a primary DNS address and the second Pihole as a secondary DNS address. And vice versa, the second Pihole gives itself as primary and the other one as secondary.
If either of the Piholes goes down, the other one will be used as a secondary DNS server and everything will continue working.
In all the years I've been running two Piholes, this incident above is the first time I've ever had a failure and that was entirely down to user error. They really are such fantastically reliable things. Having said that, even knowing how reliable they are, I still wouldn't be comfortable with just one.
I had two piholes, pihole-buster1 and pihole-buster2, the former running on a P4 and the latter on a Zero. I swapped the Zero for a Zero2 and it was just a case of moving the SD card over and it worked perfectly. I didn't expect that to work when going from a 4 to a Zero2W and I was right.
Rebuilding was easy enough, I called the new one pihole-bullseye1 and got it all set up nicely. I have various scripts running that copy files from 1 to 2 and if I need to make any changes on 1, they get replicated to 2 overnight.
Where I made a mistake was by mistyping a - for an = in /etc/dnsmasq.d/02-pihole-dhcp.conf. I didn't restart the service after editing the file on pihole-bullseye1 so it didn't show up as a problem. At 01:00 in the morning, the file was replicated over to pihole-buster2 and the FTL service restarted. Because of the typo, the services I restart failed to restart leaving it effectively down.
You see where it all went a bit rubbish and then where I recovered it the next morning.
The new one did a splendid job though and everything continued working. This was a proper trial by fire, you can see I only got it online a few hours before.
"So @Feek, how do you have two Piholes working together?" I hear you ask.
It's pretty straightforward although it sounds confusing as I type it.
My Piholes run DHCP as well as DNS so they're each configured slightly differently.
From the dashboard, go to Settings / DHCP
On the first Pihole, I have the DHCP server enabled and the range of IP addresses is set from 192.168.1.20 to 192.168.1.59
On the second Pihole, I also have the DHCP server enabled and the range of IP addresses is set from 192.168.1.60 to 192.168.1.100
That gives me a total of 80 available DHCP addresses in the pool. I have the lease time set to just 6 hours on both so there are always plenty of available leases.
The next thing I do is to edit /etc/dnsmasq.d/02-pihole-dhcp.conf and add an extra line.
The two Piholes are on 192.168.1.11 and 192.168.1.12
On the first Pihole, I add
dhcp-option=6,192.168.1.11,192.168.1.12
On the second Pihole, I add
dhcp-option=6,192.168.1.12,192.168.1.11
(then restart FTL/dns or just reboot the Pi)
That means that any device which DHCPs from the first Pihole will be given the first Pihole as a primary DNS address and the second Pihole as a secondary DNS address. And vice versa, the second Pihole gives itself as primary and the other one as secondary.
If either of the Piholes goes down, the other one will be used as a secondary DNS server and everything will continue working.
In all the years I've been running two Piholes, this incident above is the first time I've ever had a failure and that was entirely down to user error. They really are such fantastically reliable things. Having said that, even knowing how reliable they are, I still wouldn't be comfortable with just one.


 (Run it under Docker on your Nas for example)
(Run it under Docker on your Nas for example)