Caporegime
- Joined
- 18 Oct 2002
- Posts
- 33,188
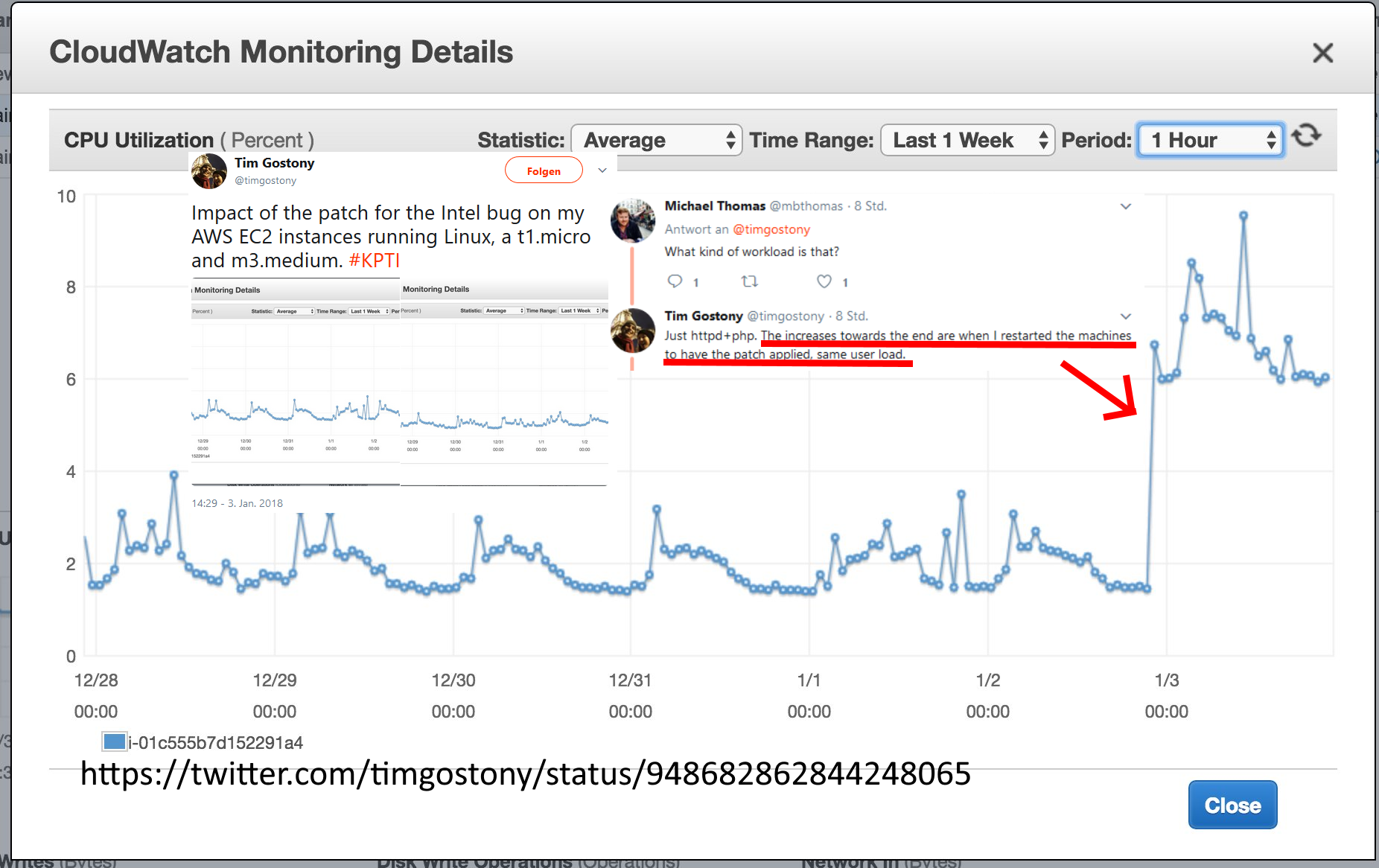
Based on benchmarks so far, the IPC difference hasn't really changed overall.
It does make Epyc more compelling for some datacenter tasks though.
I mean one of the first places to benchmark showed a 5% drop in gaming frame rates at 1080p in all the games they tested, then the article said there was no noticeable reduction in performance. Yet for Zen/coffeelake reviews when there is no framerate difference at 4k but a 5% frame rate difference at 1080p and cpu limited they go on to say Intel has a commanding 5% lead in gaming.....
THere seems to absolutely be a performance drop, but review sites are being careful not to call Intel out on it at all.