Soldato
- Joined
- 24 Sep 2015
- Posts
- 3,976
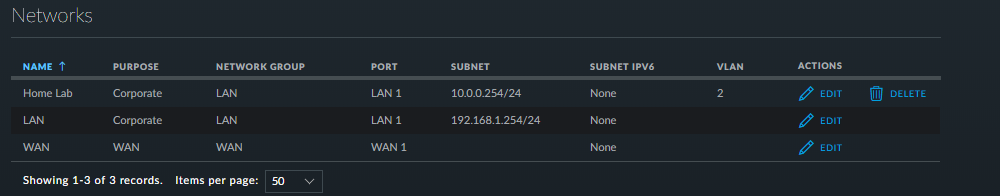
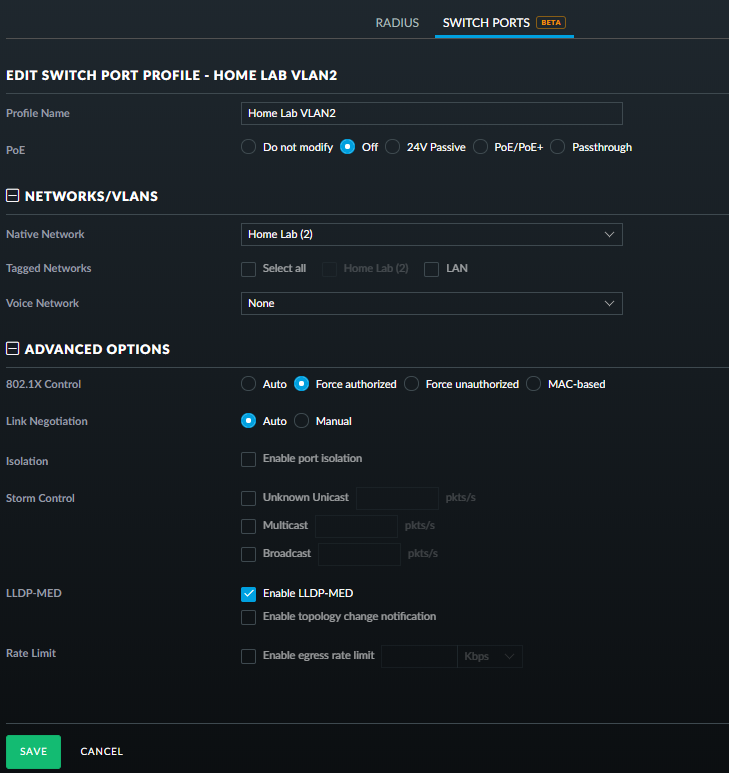
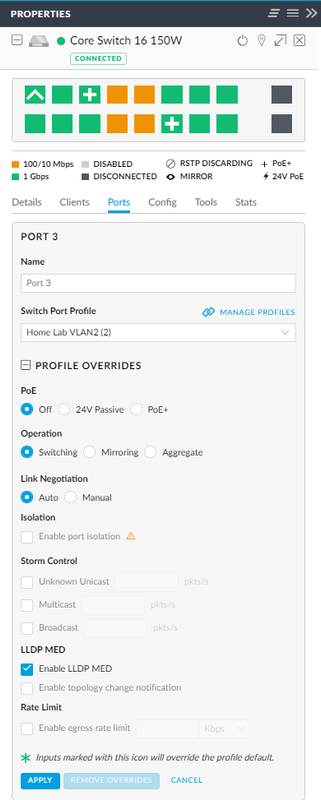
No. The older AC lite uses 24v passive PoE and the US-8 needs 802.3at in to be able to provide 802.3af out.
Also the PoE output on the US-8 is 802.3af only so you'd need a new injector to be able to power your AC lite from it.
Also the PoE output on the US-8 is 802.3af only so you'd need a new injector to be able to power your AC lite from it.