-
Competitor rules
Please remember that any mention of competitors, hinting at competitors or offering to provide details of competitors will result in an account suspension. The full rules can be found under the 'Terms and Rules' link in the bottom right corner of your screen. Just don't mention competitors in any way, shape or form and you'll be OK.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Intel bug incoming? Meltdown and Spectre exploits
- Thread starter pete910
- Start date
More options
Thread starter's postsIntel have deliberately juxtaposed two sentences praying people make a link. They also know this release will be posted by others.
But AMD are affected by one of the exploits as far as I have read (they are after all commenting on the "exploits" as a whole)
Wow that's a damn cheeky press release; factually correct that Intel are working with other companies such as AMD. But not yet factually proved that AMD have the same bug. Just wow. Unbelievable.Intel has responded:
https://newsroom.intel.com/news/intel-responds-to-security-research-findings/
They think the issue is not unique to them, not sure what this means yet.
Wow that's a damn cheely press releae; factually correct that Intel are working with other companies such as AMD. But not yet factually proved that AMD have the same bug. Just wow. Unbelievable.
AMD are affected by Spectre, but not Meltdown and Intel have not specified which exploit they are talking about, they have just said "exploits".
But AMD are affected by one of the exploits as far as I have read (they are after all commenting on the "exploits" as a whole)
Zen is not for either,
Info here for those interested
https://googleprojectzero.blogspot.co.uk/
Associate
- Joined
- 1 Feb 2009
- Posts
- 2,124
Just what I needed to push WSUS into the estate. Not ideal, but I did say it would take another wannacry level for it to be done like this.
Anyone else looking forward to patching? My team is looking at circa 20K CI's to patch
I would assume Citrix and VMware estates will have a patch applied too?
Anyone else looking forward to patching? My team is looking at circa 20K CI's to patch
I would assume Citrix and VMware estates will have a patch applied too?
I've probably only got a few hundred to patch. I don't manage the infrastructure itself but as my team manages hundreds of applications across multiple datacentres we'll need to find suitable downtime slots to patch them (ie this weekend most likely).Just what I needed to push WSUS into the estate. Not ideal, but I did say it would take another wannacry level for it to be done like this.
Anyone else looking forward to patching? My team is looking at circa 20K CI's to patch
I would assume Citrix and VMware estates will have a patch applied too?
Then next week we'll find out whether those servers are crippled enough to impact end user performance.
Caporegime
- Joined
- 18 Oct 2002
- Posts
- 33,188
Google apparently identified it as this, they created code to exploit these attacks, 4 different paths, one non malicious and 3 malicious. Intel was vulnerable to all 4 on basically every chip since the Pentium, so everything in the market and then some. AMD was only vulnerable to the non malicious attack with Zen and they said I think one of the malicious attacks worked on a A8-9600 in a non default state(I have no idea what that means but it seems to imply the system has to be in a odd state for it to work, so maybe very little risk there either).
The thing is this is the biggest risk in things like servers, which is pretty much exclusively Zen vs any Xeons. The far worse security flaw needs patching for all Intel chips and is immune on AMDs only relevant chips.
The thing is this is the biggest risk in things like servers, which is pretty much exclusively Zen vs any Xeons. The far worse security flaw needs patching for all Intel chips and is immune on AMDs only relevant chips.
But AMD are affected by one of the exploits as far as I have read (they are after all commenting on the "exploits" as a whole)
Intel are of course already in full spin mode and trying to muddy the waters by claiming that it's not just them, but clearly they're by far the worst-hit.
Niiiiiiiiice. Open source rocks
I expect I'm in for a few days of hell at work trying to schedule emergency patching on hundreds of servers
Lol, just amended my post , read as Linus but was a different maintainer

Having said that, the AUR guys have pulled it in too.
Permabanned
- Joined
- 15 May 2006
- Posts
- 4,107
- Location
- London
While at the moment with the mainline Linux kernel Git tree AMD CPUs enable x86 PTI and are treated as "insecure" CPUs, the AMD patch for not setting X86_BUG_CPU_INSECURE will end up being honored.
The patch covered in the aforelinked article has not been merged through to Linus Torvalds' Git tree. Instead, as of a short time ago, is now living within the tip/tip.git tree. In there is also defaulting PAGE_TABLE_ISOLATION to on and other recent fixes around x86 Page Table Isolation (PTI) support.
But what remains to be seen is if this work will be pulled into Linux 4.15 Git or not. We're within three weeks of the executed debut of Linux 4.15.0 stable and it isn't clear if these tip changes will be requested to be pulled into Linux 4.15 or be postponed until the start of the Linux 4.16 kernel merge window, since the safe bulk of the x86 PTI work is already in Git master. Right now the branch name doesn't indicate it's in any fixes/urgent queue nor has there been any pull request yet asking Torvalds to take it into his repository: normally tip.git master is with material for linux-next.
So we'll have to see what ends up happening in the days ahead, but regardless, at least the "AMD patch" is now sitting within a known tree that will eventually flow into the mainline Linux tree whether it be 4.15 or 4.16.
The patch covered in the aforelinked article has not been merged through to Linus Torvalds' Git tree. Instead, as of a short time ago, is now living within the tip/tip.git tree. In there is also defaulting PAGE_TABLE_ISOLATION to on and other recent fixes around x86 Page Table Isolation (PTI) support.
But what remains to be seen is if this work will be pulled into Linux 4.15 Git or not. We're within three weeks of the executed debut of Linux 4.15.0 stable and it isn't clear if these tip changes will be requested to be pulled into Linux 4.15 or be postponed until the start of the Linux 4.16 kernel merge window, since the safe bulk of the x86 PTI work is already in Git master. Right now the branch name doesn't indicate it's in any fixes/urgent queue nor has there been any pull request yet asking Torvalds to take it into his repository: normally tip.git master is with material for linux-next.
So we'll have to see what ends up happening in the days ahead, but regardless, at least the "AMD patch" is now sitting within a known tree that will eventually flow into the mainline Linux tree whether it be 4.15 or 4.16.
Amds architecture may well be able to fix this issue since they can do a lot more at the microcode level than intel can.
However being vulnerable to even one of the exploits means they will have to suffer the performance hit of the patch hopefully for the short term.
However being vulnerable to even one of the exploits means they will have to suffer the performance hit of the patch hopefully for the short term.
Permabanned
- Joined
- 15 May 2006
- Posts
- 4,107
- Location
- London
Warning to all those using Antivirus software
The windows patch that Microsoft are forcing out may break your AV software....:
The windows patch that Microsoft are forcing out may break your AV software....:
Amds architecture may well be able to fix this issue since they can do a lot more at the microcode level than intel can.
However being vulnerable to even one of the exploits means they will have to suffer the performance hit of the patch hopefully for the short term.
Not sure which vulnerability you mean but, the patch that causes the perf hit is solely for PTI code on intel CPUS.
Associate
- Joined
- 7 Aug 2017
- Posts
- 415
- Location
- location location
Intel has responded:
https://newsroom.intel.com/news/intel-responds-to-security-research-findings/
They think the issue is not unique to them, not sure what this means yet.
Grrr - that's just PR fluff that's full of weaselly statements for damage limitation only.
I recommend the Meltdown FAQ (Spectre FAQ is actually the same page; it covers and distinguishes both) and this Google blogpost for useful information, including a flag you can toggle in Chrome (and other chromium-based browsers like Opera and Vivaldi) to protect against Spectre right now. If you're into technical details, that blogpost also links to the Project Zero blog which has details on both attacks.
Amds architecture may well be able to fix this issue since they can do a lot more at the microcode level than intel can.
Have you got any sources to back up this assertion about microcode capability?
However being vulnerable to even one of the exploits means they will have to suffer the performance hit of the patch hopefully for the short term.
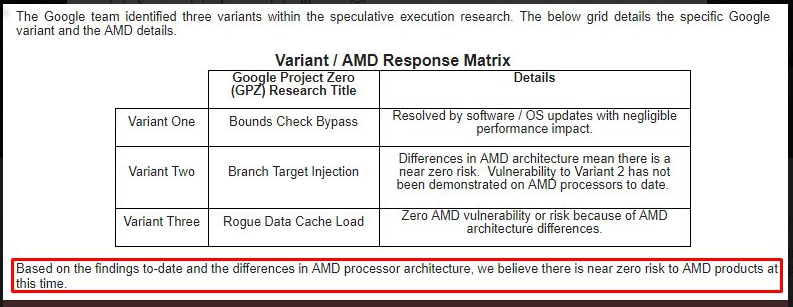
Meltdown (a.k.a. Variant 3: rogue data cache load (CVE-2017-5754)) is the one of immediate concern, as it is system-wide and the patch for this (KPTI) has a significant impact on performance for some scenarios, particularly those that make frequent syscalls. Many Intel CPUs are known to need this patch; select ARM CPUs (well - just Cortex A75 according to this) are affected (but the performance impact isn't clear of the ARM variant of the patch), and AMD claim to be unaffected by this. The Linux kernels that get released may well exclude AMD from KPTI.
Spectre (a.k.a. Variant 1: bounds check bypass (CVE-2017-5753) and Variant 2: branch target injection (CVE-2017-5715)) isn't addressed by KPTI as it's to do with isolation between applications; this is addressed by application software patches and other mitigation measures; the performance penalty depends on the application and might not be significant.
Intel has responded:
https://newsroom.intel.com/news/intel-responds-to-security-research-findings/
They think the issue is not unique to them, not sure what this means yet.
They don't, they just hope that if they word their FUD right you will



