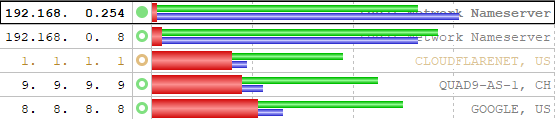
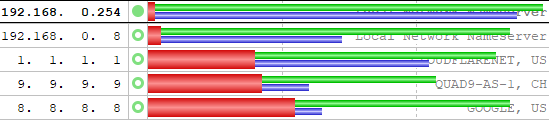
I've got two of those little mini Dells already, one's an i5-7500T which I think was originally a 5th gen but I upgraded the CPU and when it's running, I can hear the fan most of the time. The other one is an i7-13700T and I sometimes hear that when it's running. They're both normally switched off and run ham radio software when I specifically need a Windows PC. The second one was supposed to replace the first one but I've got a couple of things I've not been able to shift over so that's why I still have two 
I suppose a third wouldn't be out of the question.

I suppose a third wouldn't be out of the question.