You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Do you change DNS?
- Thread starter danlightbulb
- Start date
More options
Thread starter's postsDid you get a chance to play with this yet, Chris? It makes a nice difference to the stats and usability of the dash.Cheers, will check it out tomorrow.

No mate not yet. Family…Did you get a chance to play with this yet, Chris? It makes a nice difference to the stats and usability of the dash.
Understandable mate. Family first!No mate not yet. Family…
I did some research into this and it seems pointing your DNS towards a third party DNS resolver (such as Quad9, Cloudflare) encrypts the DNS queries, but after you acquire the IP, you immediately ask for the IP and name of the site in clear text through your ISP. So the ISP can determine where you are visiting anyway.
On the other hand, running your own recursive resolver in Unbound, you eliminate your data going to a third party DNS resolver, however all your queries are sent in plaint text to authoritative nameservers, which your ISP can see. Repeat queries though will then come from the Unbound cache.
So in both scenarios the ISP can determine where you are visiting, so while there is no true privacy, hosting your own recursive resolver would be the better option as you eliminate sending your data to a 3rd party company.
Other factors would be the speed of resolving queries and if you require some type of filtering, either through third party DNS resolvers or using pihole/adguard.
Have I understood this correctly?
On the other hand, running your own recursive resolver in Unbound, you eliminate your data going to a third party DNS resolver, however all your queries are sent in plaint text to authoritative nameservers, which your ISP can see. Repeat queries though will then come from the Unbound cache.
So in both scenarios the ISP can determine where you are visiting, so while there is no true privacy, hosting your own recursive resolver would be the better option as you eliminate sending your data to a 3rd party company.
Other factors would be the speed of resolving queries and if you require some type of filtering, either through third party DNS resolvers or using pihole/adguard.
Have I understood this correctly?
In a nutshell yes, only true way to hide from your isp is using a VPN for everything, but then again do you trust the VPN provider not to log data.I did some research into this and it seems pointing your DNS towards a third party DNS resolver (such as Quad9, Cloudflare) encrypts the DNS queries, but after you acquire the IP, you immediately ask for the IP and name of the site in clear text through your ISP. So the ISP can determine where you are visiting anyway.
On the other hand, running your own recursive resolver in Unbound, you eliminate your data going to a third party DNS resolver, however all your queries are sent in plaint text to authoritative nameservers, which your ISP can see. Repeat queries though will then come from the Unbound cache.
So in both scenarios the ISP can determine where you are visiting, so while there is no true privacy, hosting your own recursive resolver would be the better option as you eliminate sending your data to a 3rd party company.
Other factors would be the speed of resolving queries and if you require some type of filtering, either through third party DNS resolvers or using pihole/adguard.
Have I understood this correctly?
I use Recurse Unbound myself.
the idea behind quad9 etc is to stop anyone snooping into these packets as they leave your home and onto the DNS servers.
Understood.In a nutshell yes, only true way to hide from your isp is using a VPN for everything, but then again do you trust the VPN provider not to log data.
I use Recurse Unbound myself.
the idea behind quad9 etc is to stop anyone snooping into these packets as they leave your home and onto the DNS servers.
I looked into Quad9 and on their website they have Global Cyber Alliance listed on their sponsors page as one of their founding organisations.
Global Cyber Alliance has listed on their website, in their founders and funders section, City of London Police and the Manhattan District Attorney's Office amongst others.
Interesting.
Last edited:
Soldato
- Joined
- 24 Mar 2018
- Posts
- 3,563
- Location
- Brighton
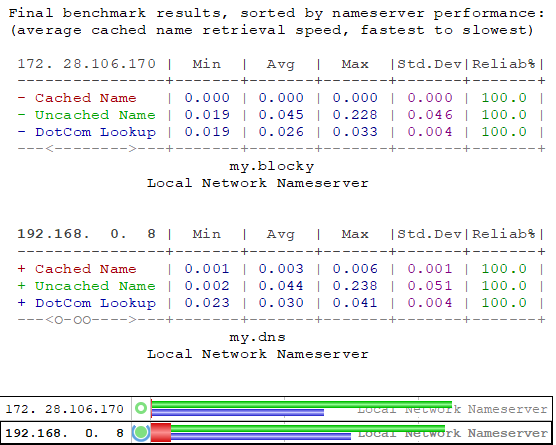
It's nippy I'll give it that.. but that was Local Machine vs WiFi fetch from my pihole to be fair. I would need to test more!

You're talking about SNI, the server name indication. It's possible to encrypt this also, and efforts are well underway. For example, Cloudflare, Mozilla/Firefox, Chrome(ium) browsers, Apple and others are now working to close this privacy loophole. A few years ago, the effort started with ESNI (encrypted SNI) but that protocol was later dropped and rehashed into a broader more private ECH (encrypted client hello). If you enable DoH and ECH in your browser and visit a naughty website (ahoy...) on a UK ISP that bans such sites, suddenly you'll find they load fine even without a VPN - provided they're on Cloudflare, as no other big host enabled ECH yet.Have I understood this correctly?
Last edited:
What upstream is blocky pointing to?It's nippy I'll give it that.. but that was Local Machine vs WiFi fetch from my pihole to be fair. I would need to test more!

Soldato
- Joined
- 24 Mar 2018
- Posts
- 3,563
- Location
- Brighton
I just chucked in 9.9.9.9-1.1.1.1 as a secondary. vs root on the my.dns. Like I said blocky is running on my local machine with me though hence the faster cache etc.
i tried blocky last night, seems ok, nice feature set but lack of native gui, makes it hard to have as main dns server
I then tried Technitium and it seems really good, one big thing for me is it has persistent cache out of the box, something unbound cannot do without 3rd party database, literally one tick box to enable it!
Its recursive like Unbound with DOH support for forwarding if you wish and has built in replication to a secondary Technitium server with proper replication, something AGH and Pihole cannot do without addons/extra tools.
Technitium of course has room to grow but seems good, dev is active, I will test it for a while, this could replace my Adguard Home.
2 Minors are no Gui Dark Mode and also no way to see response times like Adguard shows but have been told its on the way.
I then tried Technitium and it seems really good, one big thing for me is it has persistent cache out of the box, something unbound cannot do without 3rd party database, literally one tick box to enable it!
Its recursive like Unbound with DOH support for forwarding if you wish and has built in replication to a secondary Technitium server with proper replication, something AGH and Pihole cannot do without addons/extra tools.
Technitium of course has room to grow but seems good, dev is active, I will test it for a while, this could replace my Adguard Home.
2 Minors are no Gui Dark Mode and also no way to see response times like Adguard shows but have been told its on the way.
Last edited:
Soldato
- Joined
- 24 Mar 2018
- Posts
- 3,563
- Location
- Brighton
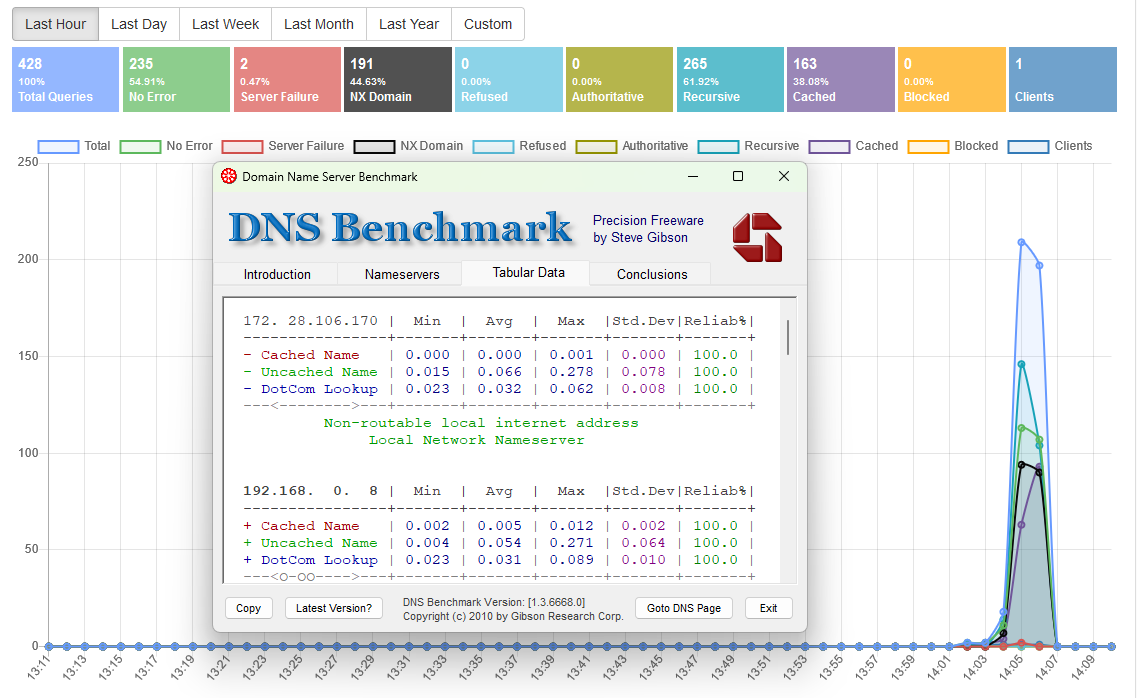
I was going to try it, but lowest spec was arm7 so it I just tried blocky again on RPi1 B+ (amr6) Turbo Mode. pretty much the same although the cache was 8ms vs pihole 5ms.i tried blocky last night, seems ok, nice feature set but lack of native gui, makes it hard to have as main dns server
I then tried Technitium and it seems really good, one big thing for me is it has persistent cache out of the box, something unbound cannot do without 3rd party database, literally one tick box to enable it!
Its recursive like Unbound with DOH support for forwarding if you wish and has built in replication to a secondary Technitium server with proper replication, something AGH and Pihole cannot do without addons/extra tools.
Technitium of course has room to grow but seems good, dev is active, I will test it for a while, this could replace my Adguard Home.
2 Minors are no Gui Dark Mode and also no way to see response times like Adguard shows but have been told its on the way.
I will try it though when I spin something up later!
systemd now available on wsl2.. ok
So....
Not bad either!
Last edited:
2 Minors are no Gui Dark Mode and also no way to see response times like Adguard shows but have been told its on the way.
If you use Apple devices then have a look at Noir on the App store, it's a Safari plugin that styles most websites with a dark mode.
You won't go wrong. They are reliable and have excellent malware and threat blocking that's basically unmatched, especially for free.Never heard of quad9 until I just read this thread. I'll give it a try, always used google for some reason or another..
Hopefully not a classic case of "if its not broken - why did you fix it..."
Guys, I updated my Blocky tutorial post HERE. Now it's a single Docker Compose project that includes Blocky, Grafana and Prometheus all in one, with all the configs included to get the dashboard working. I'll get it all posted onto Docker Hub and/or Github at some point, but for now the bones are there - just more copy/paste required for now lol.

Last edited:
Ive settled on Technitium for now, created 2 instances on my proxmox cluster, works really well and i like to give the under dog a chance. the persistent cache is a killer feature, can reboot at will and not have to start buiding cache again.
Soldato
- Joined
- 24 Mar 2018
- Posts
- 3,563
- Location
- Brighton
I was using it the other day, seems fast enough. It also queries root and DNSSEC out of the box and I don't need to read a book full of rubbish to get it to run properly.
Although I am looking for something that Encrypts HTTPS queries end to end with add blocking at the same time without needing to read a book from my local network.
Although I am looking for something that Encrypts HTTPS queries end to end with add blocking at the same time without needing to read a book from my local network.
does end to end https encryption exist? i thought only VPN would do this.I was using it the other day, seems fast enough. It also queries root and DNSSEC out of the box and I don't need to read a book full of rubbish to get it to run properly.
Although I am looking for something that Encrypts HTTPS queries end to end with add blocking at the same time without needing to read a book from my local network.

