Soldato
- Joined
- 24 Mar 2018
- Posts
- 3,445
- Location
- Brighton
No Idea never tried...
I did some research into this and it seems pointing your DNS towards a third party DNS resolver (such as Quad9, Cloudflare) encrypts the DNS queries, but after you acquire the IP, you immediately ask for the IP and name of the site in clear text through your ISP. So the ISP can determine where you are visiting anyway.
On the other hand, running your own recursive resolver in Unbound, you eliminate your data going to a third party DNS resolver, however all your queries are sent in plaint text to authoritative nameservers, which your ISP can see. Repeat queries though will then come from the Unbound cache.
So in both scenarios the ISP can determine where you are visiting, so while there is no true privacy, hosting your own recursive resolver would be the better option as you eliminate sending your data to a 3rd party company.
Other factors would be the speed of resolving queries and if you require some type of filtering, either through third party DNS resolvers or using pihole/adguard.
Have I understood this correctly?
Quad9 is a non-profit and sponsored by those agencies and more with a view to reducing cybercrime. That's why they ended up by far the best anti-malware/anti-botnet/anti-everything-bad DNS provider by far, even significantly in excess of Cloudflare's malware blocking service. They're not actually affiliated (in the sense you mean) with LEA.thanks for this posting, I asked something similar a while back but the answers I got from another board made it sound like an almost yes and no answer... I always felt there was something still popping up on the ISP side.
If you trust your VPN provider they usually offer a DNS server which is what I do anyhow, for rest of devices that require access to clear net I tend to use quad9/cloudflare but now at least I know even that is not safe for data leakage.
Think ill switch to Cloudflare for now and check into other DNS options later on, maybe quad9 is just minus one 9 and all data goes to City of London Police and the Manhattan District Attorney's Office.
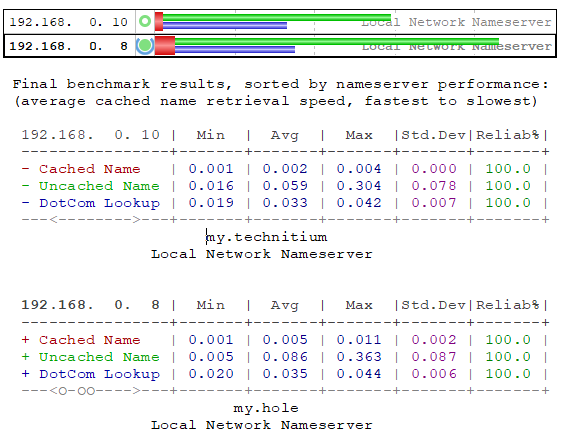
been using Techitium since 28th Jan (in recursive mode) and I can already tell the difference in browsing speeds compared to AGH, it is blazing fast.Ive settled on Technitium for now, created 2 instances on my proxmox cluster, works really well and i like to give the under dog a chance. the persistent cache is a killer feature, can reboot at will and not have to start buiding cache again.
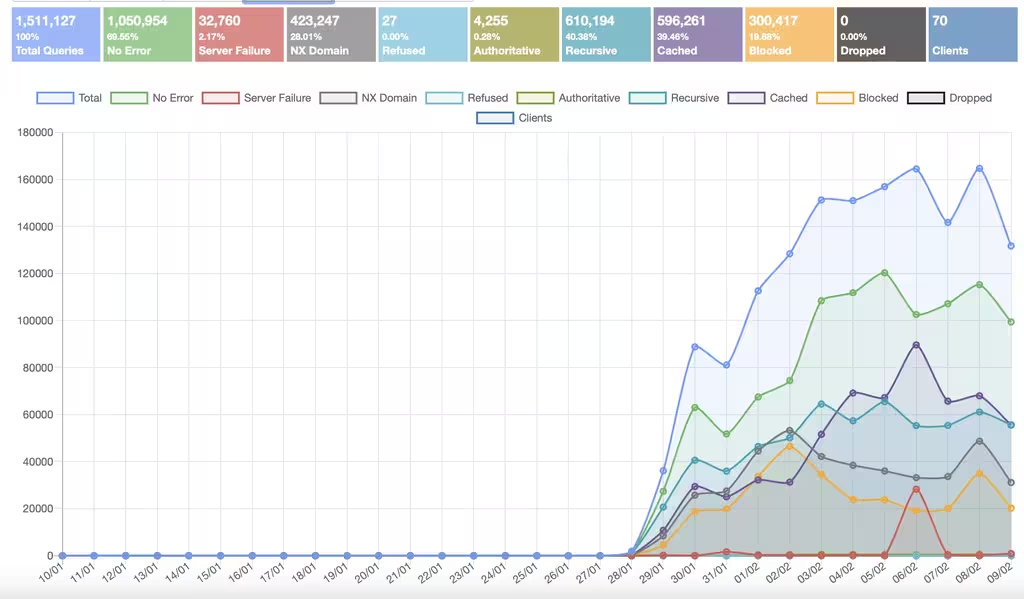
I really like Technitium, and you're right - it's very fast. For my use case I'd want/need per client blocklists. There *is* a plugin for that, but the syntax is a little convoluted and it doesn't appear there's any quick way to do it, so it's on the pile for Future Me.I can highly recommend it!
My main issue is their syntax for the advanced blocking app. The regular blocking doesn't allow per-client list choices, and the advanced blocking app doesn't accept plain text IP ranges. I have no problem with manual config (see: Blocky), but for the Technitium advanced blocking app everything has to be done the 'long way'. My network is just a regular /24, but there's six of us - me, my wife, and four kids. We all have iPhones/iPads/laptops/PCs/smart watch etc, then there's smart devices and FireTV Sticks, plus CCTV cameras, plus IoT devices, plus multiple physical servers, and so on. Because of client config requirements in AGH, running DHCP was no good - I needed each client to stay recognisable over the long term. I ended up just basically dumping DHCP for resident devices, and assigning everyone 10 IP addresses:I would have to agree with what you both said, Technitium is very fast and easy to implement on various systems. the instructions are well written and clear.
You have to hand it to them though, it would take me quite a while to re-rebuild my current deployment with Unbound/Pihole vs Technitium in just a few minutes to deploy the same features more or less.
--- Core networking equipment
10.100.0.1 - border router running VyOS 1.3 LTS, CLI only
10.100.0.2 - core managed/L3 switch
--- Personal device ranges
10.100.0.10 to 10.100.0.19 - My devices
10.100.0.20 to 10.100.0.29 - Wife's devices
10.100.0.30 to 10.100.0.39 - Eldest's devices
10.100.0.40 to 10.100.0.49 - Child 2's devices
10.100.0.50 to 10.100.0.59 - Child 3's devices
10.100.0.60 to 10.100.0.69 - Child 4's devices
10.100.0.70 to 10.100.0.79 - Old/random/inherited devices
----------
Legacy server IP assignments from before the re-segment, carried up 100 IPs out of the' family' range, but kept memorable.
That is, 10.100.0.5 became 10.100.0.150, 10.100.0.12 became 10.100.0.152 etc:
--- Printers ---
10.100.0.111 - HP LaserJet printer
10.100.0.112 - Epson sublimation printer (wife's projects)
10.100.0.115 - Ruckus R710 enterprise WiFi AP
--- CCTV and servers ---
10.100.0.142 - Hikvision 4K CCTV camera (front of house)
10.100.0.143 - Hikvision 4k CCTV camera (side of house)
10.100.0.144 - Hikvision 4k CCTV camera (rear of house)
10.100.0.150 - DiskStation NAS (CCTV surveillance station / NVR, primary Docker host fronting domain services, downloaders, *arrs. Vaultwarden etc)
10.100.0.152 - Raspberry Pi 3B (secondary LAN DNS, running DietPi)
10.100.0.153 - Radxa Rock 5 model B (primary LAN DNS, reverse proxy for my domain, Docker host etc)
--- Media devices ---
10.100.0.180 - TiVO v6 Virgin box (downstairs)
10.100.0.181 - TiVO v6 Virgin box (upstairs)
10.100.0.190 - FireTV Stick 4K (upstairs)
10.100.0.191 - FireTV Stick 4K (downstairs)
10.100.0.192 - Ring doorbell (front door)
10.100.0.193 - Echo Show 5 (freebie)
10.100.0.199 - Google Nest Mini (freebie)
--- DHCP range for visitors and guests, on segregated guest AP with captive portal
10.100.0.200 to 10.100.0.254Eldest child: 10.100.0.30-10.100.0.39; ads/malware/gambling. However, Technitium's Advanced Blocking app demands explicit IPs or CIDR networks, not plain text IP ranges. The closest I can come to what is a few intuitive lines in Blocky is to either list every IP between 10.100.0.10 and 10.100.0.70 and name them repeatedly into 'network groups' (me, me, me, me, wife, wife, wife etc) or convert the ranges to awkward CIDR blocks... And yes, I got around to it today after all - because posting here that I was putting it off irked me enough to actually do it haha!{
"enableBlocking": true,
"blockListUrlUpdateIntervalHours": 12,
"networkGroupMap": {
"0.0.0.0/0": "default",
"10.100.0.30/31": "eldest",
"10.100.0.32/29": "eldest",
"10.100.0.40/29": "kids",
"10.100.0.48/28": "kids",
"10.100.0.64/30": "kids",
"10.100.0.68/31": "kids"
},
"groups": [
{
"name": "default",
"enableBlocking": true,
"allowTxtBlockingReport": true,
"blockAsNxDomain": false,
"blockingAddresses": [
"0.0.0.0",
"::"
],
"allowed": [],
"blocked": ["dns.google", "dns.google.com", "dns.opendns.com", "dns.cloudflare-dns.com"],
"allowListUrls": [],
"blockListUrls": [],
"allowedRegex": [],
"blockedRegex": [],
"regexAllowListUrls": [],
"regexBlockListUrls": [],
"adblockListUrls": ["https://raw.githubusercontent.com/hagezi/dns-blocklists/main/adblock/pro.plus.txt", "https://raw.githubusercontent.com/hagezi/dns-blocklists/main/adblock/tif.txt"]
},
{
"name": "eldest",
"enableBlocking": true,
"allowTxtBlockingReport": true,
"blockAsNxDomain": false,
"blockingAddresses": [
"0.0.0.0",
"::"
],
"allowed": [],
"blocked": ["dns.google", "dns.google.com", "dns.opendns.com", "dns.cloudflare-dns.com"],
"allowListUrls": [],
"blockListUrls": [],
"allowedRegex": [],
"blockedRegex": [],
"regexAllowListUrls": [],
"regexBlockListUrls": [],
"adblockListUrls": ["https://raw.githubusercontent.com/hagezi/dns-blocklists/main/adblock/pro.plus.txt", "https://raw.githubusercontent.com/hagezi/dns-blocklists/main/adblock/tif.txt", "https://raw.githubusercontent.com/hagezi/dns-blocklists/main/adblock/anti.piracy.txt", "https://raw.githubusercontent.com/hagezi/dns-blocklists/main/adblock/gambling.txt"]
},
{
"name": "kids",
"enableBlocking": true,
"allowTxtBlockingReport": true,
"blockAsNxDomain": false,
"blockingAddresses": [
"0.0.0.0",
"::"
],
"allowed": [],
"blocked": ["dns.google", "dns.google.com", "dns.opendns.com", "dns.cloudflare-dns.com"],
"allowListUrls": [],
"blockListUrls": [],
"allowedRegex": [],
"blockedRegex": [],
"regexAllowListUrls": [],
"regexBlockListUrls": [],
"adblockListUrls": ["https://raw.githubusercontent.com/hagezi/dns-blocklists/main/adblock/pro.plus.txt", "https://raw.githubusercontent.com/hagezi/dns-blocklists/main/adblock/tif.txt", "https://nsfw.oisd.nl", "https://raw.githubusercontent.com/hagezi/dns-blocklists/main/adblock/anti.piracy.txt", "https://raw.githubusercontent.com/hagezi/dns-blocklists/main/adblock/gambling.txt", "https://raw.githubusercontent.com/hagezi/dns-blocklists/main/adblock/nosafesearch.txt"]
}
]
}
The Dev is open to requests/ideas, post here: https://github.com/TechnitiumSoftware/DnsServer/discussions/categories/ideasMy needs are as fast as I can get vs power usage, it would appear Technitium wins in that context. Lets hope they add better functionality/features soon!
Cache wins everytime in this test at least vs pihole.

How does this actually block malware? I'm sure you can still download dodgy apps and get viruses. Does it just stop people going to torrent sites etc by pointing them back to local host or error 404?I'm using Cloudflare malware blocking, no idea if it actually does the job. 1.1.1.2 and 1.0.0.2.
It returns null replies for queries that would result in known bad addresses (C&C servers, phishing, malware delivery etc). As previously noted, however, its efficacy is woeful compared to Quad9 (9.9.9.9, 2620:fe::fe).How does this actually block malware? I'm sure you can still download dodgy apps and get viruses. Does it just stop people going to torrent sites etc by pointing them back to local host or error 404?

