Just looked at their
help page on this and it's signature based presumably comparing a hash of the IP address and port you're accessing against their database and blocking the connection if it's on the list. This is very unlikely to be any more up-to-date than the safe browsing stuff already implemented in your browser with the advantage being that your browser knows the URL being accessed and can see the data outside of the TLS encryption. There's a very slim chance that this signature based detection might pick up some command-and-control (c2) botnet traffic but I wouldn't bet on it.
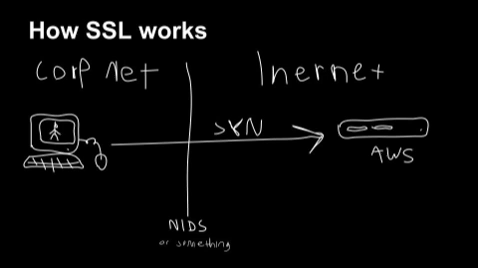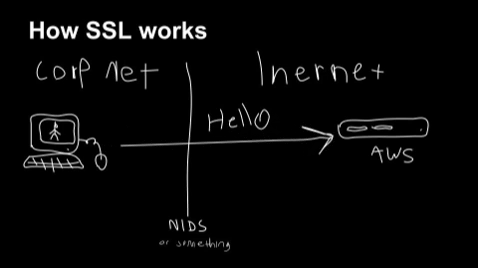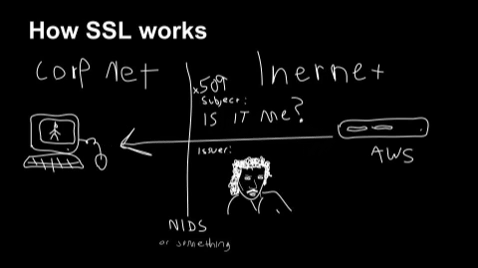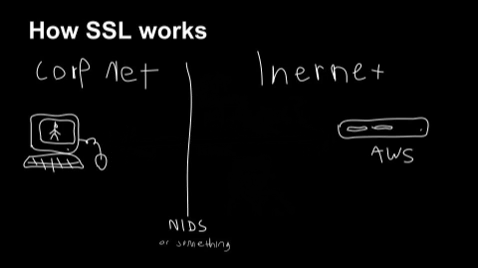
Trying to solve problems by scanning stuff passing through the network edge is pretty pointless, especially in a work setting where people take their laptops home.
Rich Threat Intelligence and Context Portal Knowing what types of threats exist is no longer enough to protect your people, data, and brand. Emerging Threat …

www.proofpoint.com